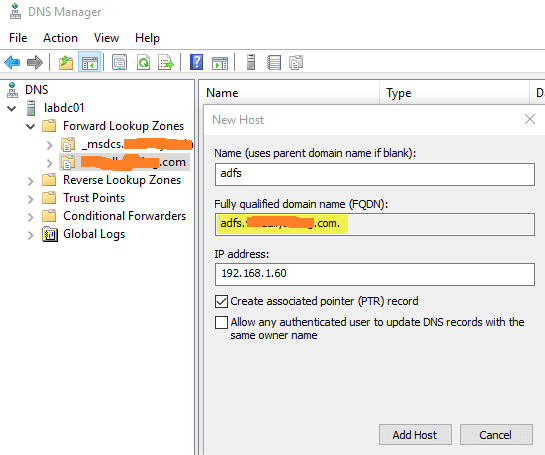
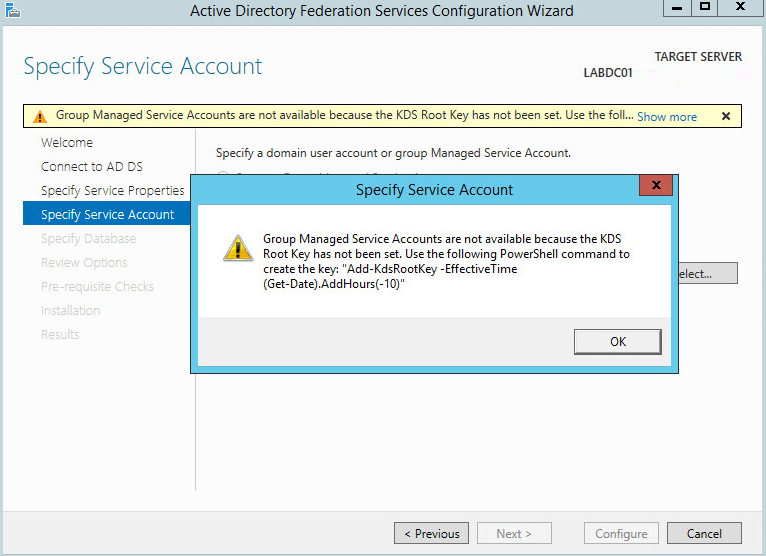
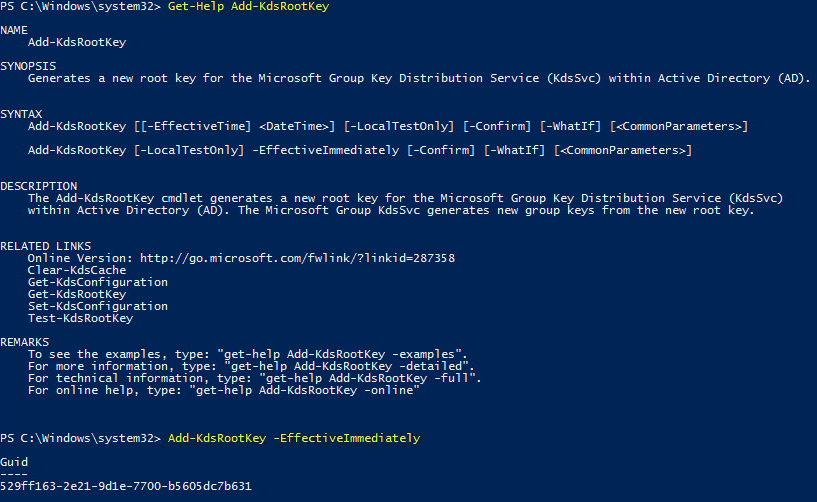
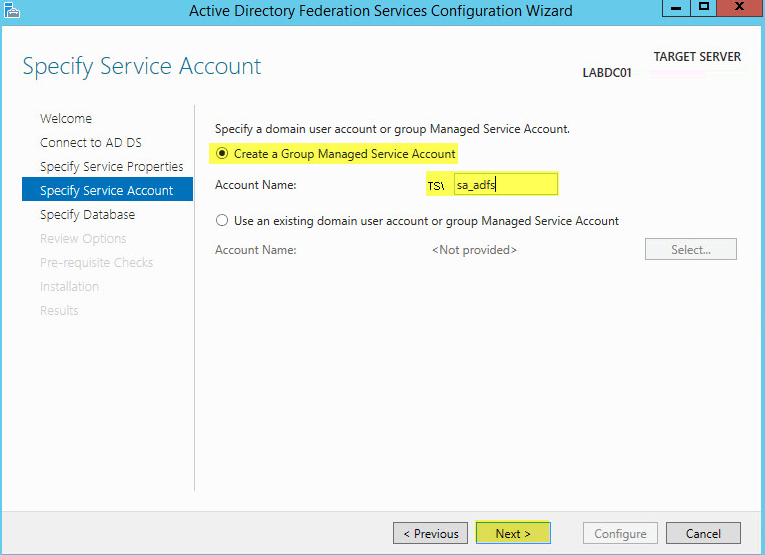
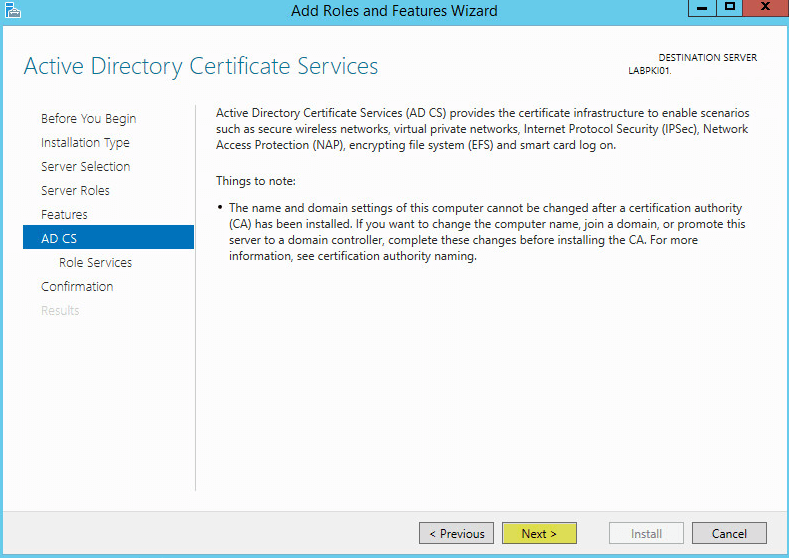
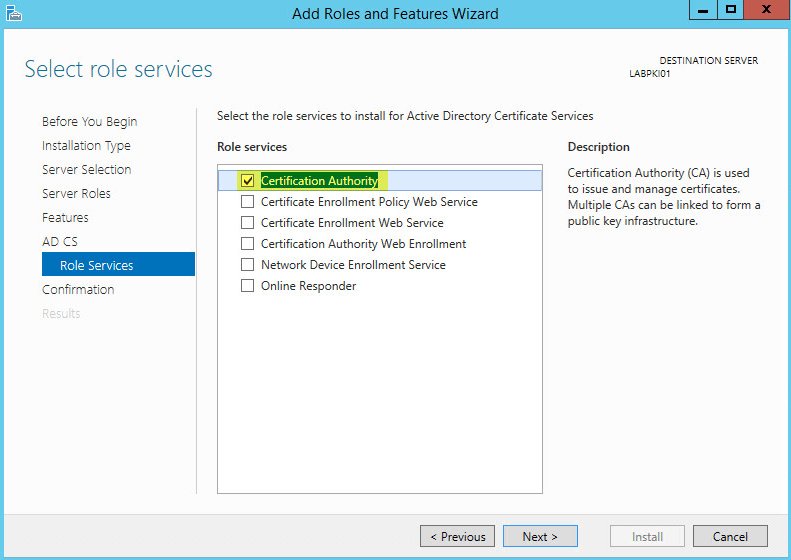
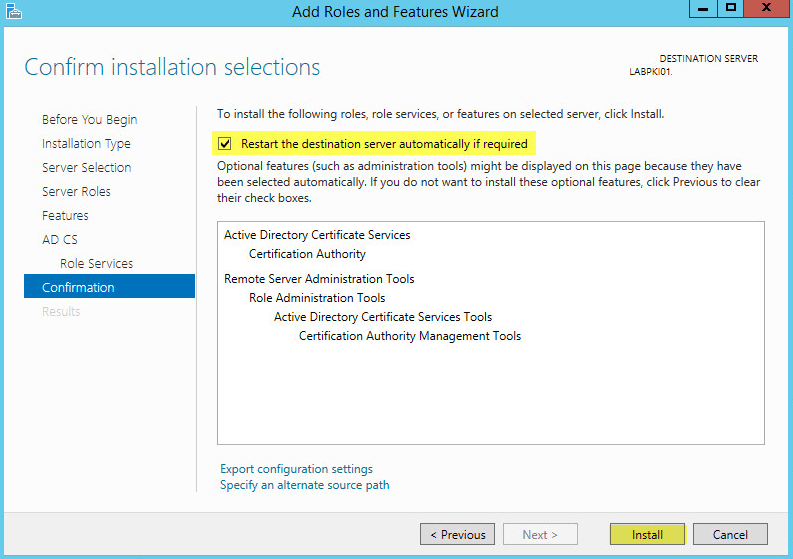
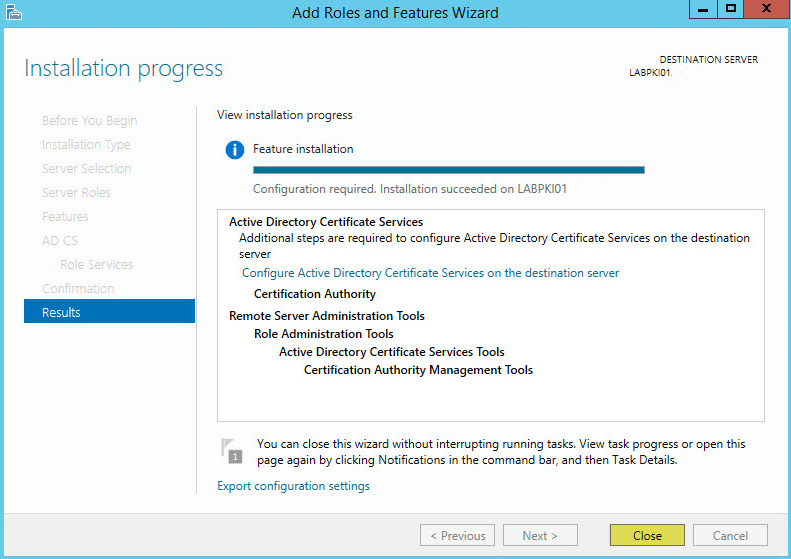
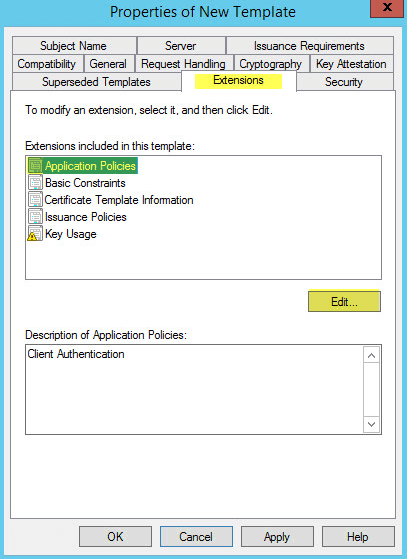
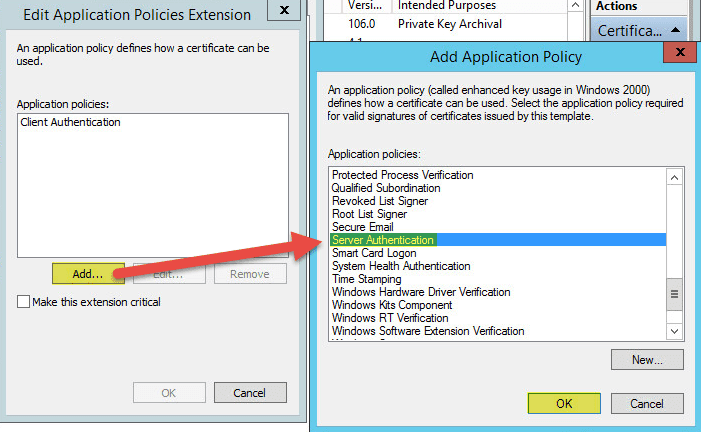
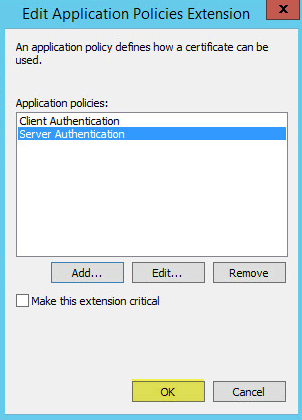
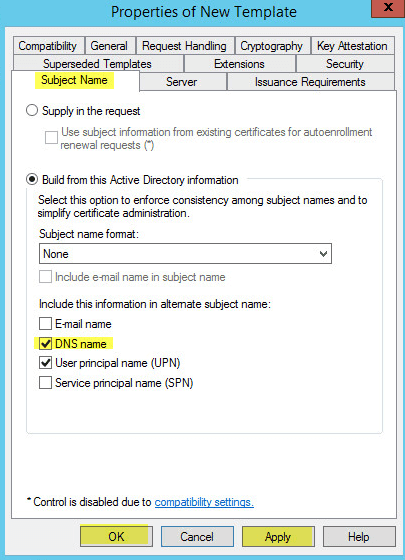
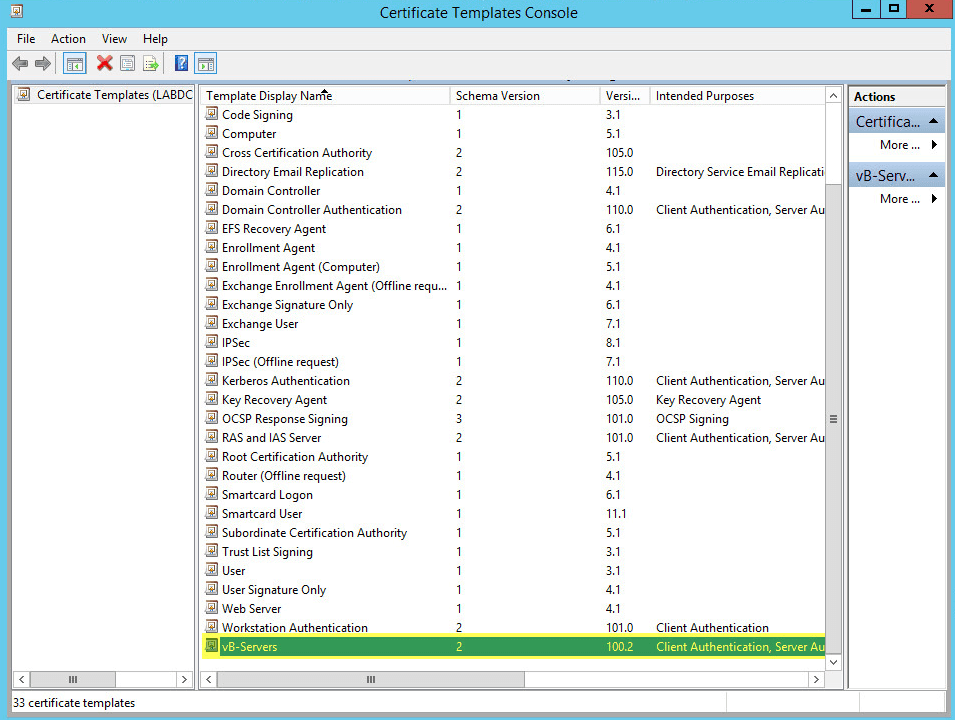
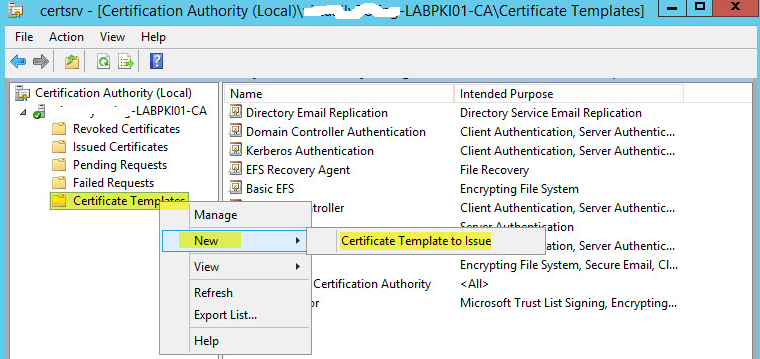
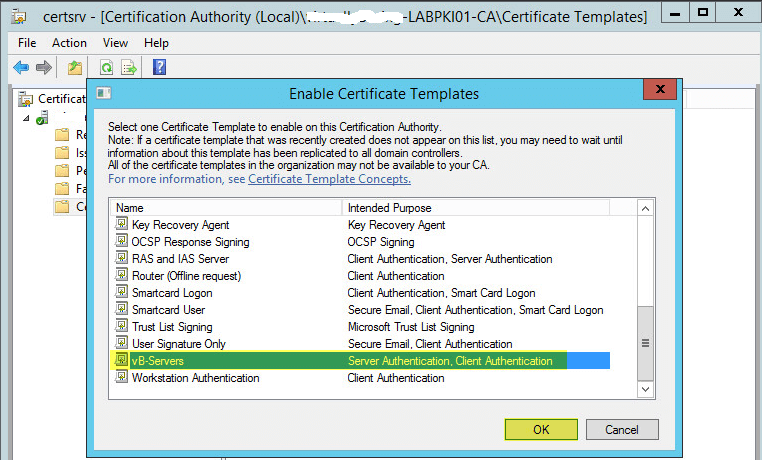
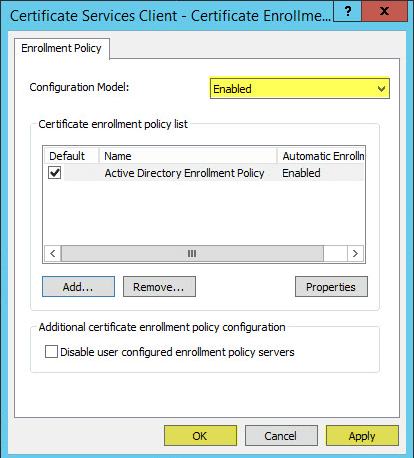
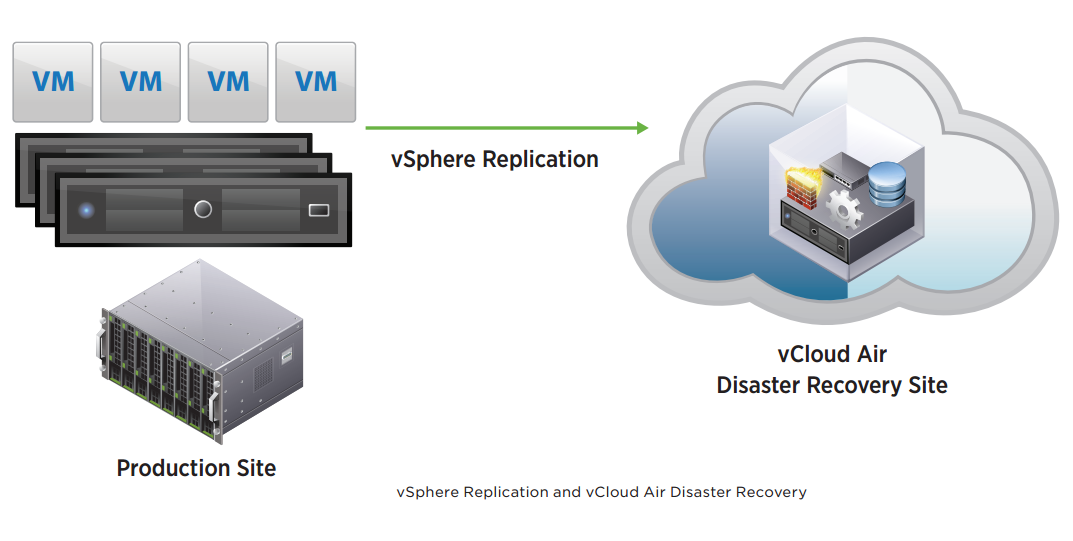
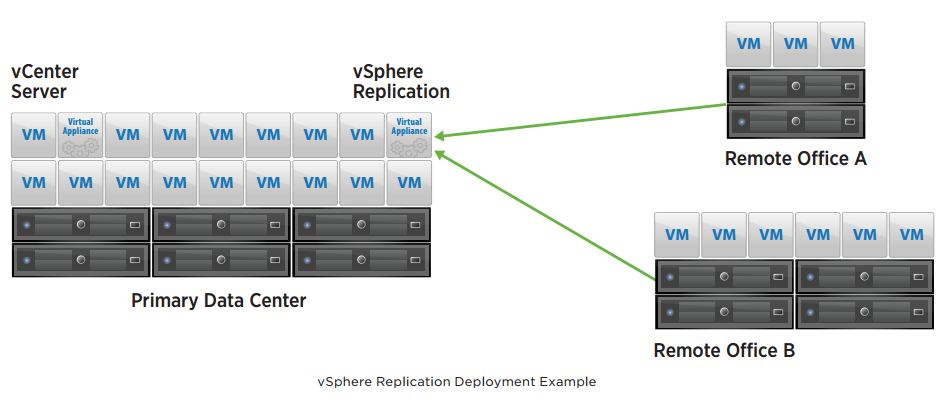
This guide will walk you through the steps to install FreeIPA (Directory Server) on a CentOS 7 server in order to set up centralized authentication for Linux distributions. You may also refer implementing in a mixed environment (Windows/Linux) from the following
link
FreeIPA is an open-source centralized authentication and security solution for Linux distributions which provides account management and centralized authentication, similar to Windows Active Directory. FreeIPA is built on top of multiple open source projects including the 389 Directory Server, MIT Kerberos, and SSSD.
FreeIPA has clients for CentOS 7, Fedora, and Ubuntu 14.04/16.04. These clients make it pretty straightforward to add machines into your IPA domain. Other operating systems can authenticate against FreeIPA using SSSD or LDAP.
Prerequisites
To follow the steps mention in this guide, you will need:
- One CentOS 7 server (bare-metal or virtual) with at least 1 GB of Memory.
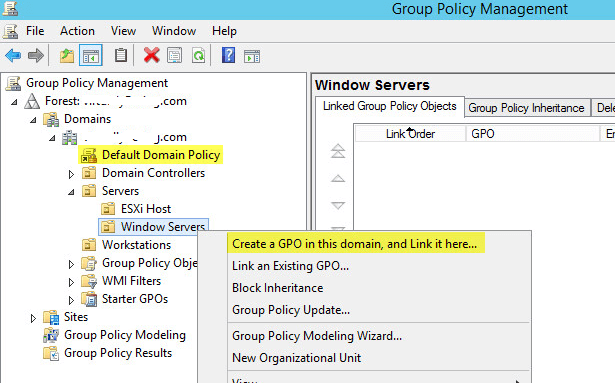
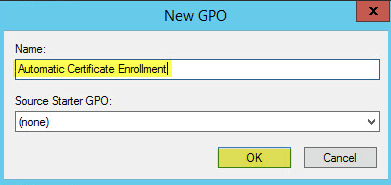
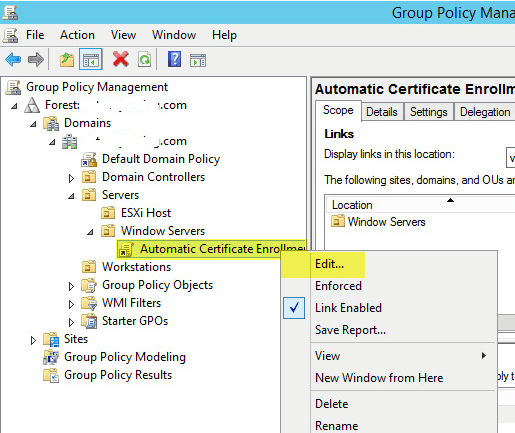
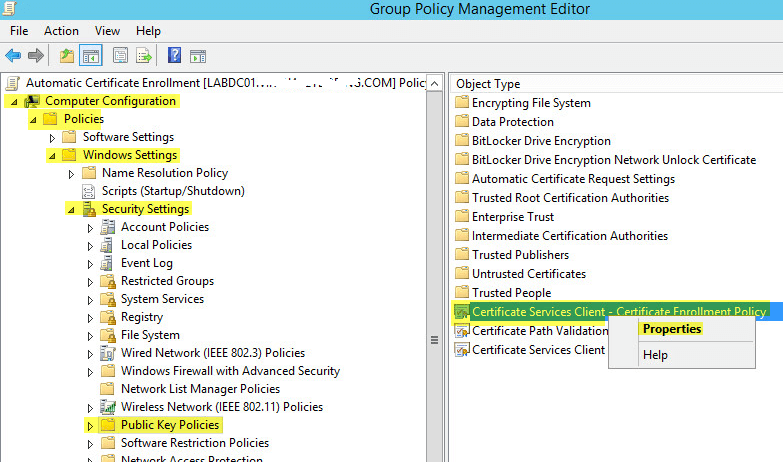
Preparing the IPA Server
To begin with the installation, first we need to do a few tasks to make sure the CentOS 7 server is ready to run FreeIPA. Specifically, we'll set the server hostname, update the system packages, check that the DNS records and make sure that the firewall will allow traffic to FreeIPA.
To start, the hostname of your server will need to match your fully qualified domain name (FQDN) for FreeIPA to function correctly. We'll be using ipa.example.com as the FQDN throughout this guide.
You can either set the hostname when you install the CentOS 7 server or set it from the command line after the CentOS 7 server is installed, using the following hostname command:
# hostname ipa.example.org
Now, update the package repository with yum.
Next, open the required ports for FreeIPA in the firewall.
# firewall-cmd --permanent --add-port={80/tcp,443/tcp,389/tcp,636/tcp,88/tcp,464/tcp,53/tcp,88/udp,464/udp,53/udp,123/udp}Reload the firewall so the changes will take effect.
Finally, you need to verify that the DNS names resolve properly. You can use the dig command for this. Install the bind-utils package to get dig and other DNS testing utilities.
Then use dig to check the A record.
# dig +short ipa.example.org A
This should return your_server_ipv4.
If you have IPv6 enabled, you can test the AAAA record the same way.
# dig +short ipa.example.org AAAA
This should return your_server_ipv6.
You can also test the reverse lookup. This tests whether you can resolve the hostname from the IP address.
# dig +short -x your_server_ipv4
# dig +short -x your_server_ipv6
These should both return ipa.example.com.
FreeIPA makes heavy use of DNS, so in the next step, we'll make sure our server meets the specific DNS requirements FreeIPA needs to work properly.
Setting Up DNS
All machines running FreeIPA must use fully qualified domain names (FQDNs) as their hostnames, which we set up in the above step. Additionally, the hostname of each server must resolve to its IP address, not to localhost.
You can find the server IP addresses using the ip command.
This should produce output similar to the following:
2: eth0: mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:00:00:00:00:00 brd ff:ff:ff:ff:ff:ff
inet 111.111.111.111/18 brd 111.111.111.255 scope global eth0
valid_lft forever preferred_lft forever
inet6 1111:1111:1111:1111::1111:1111/64 scope global
valid_lft forever preferred_lft forever
Now we need to change the host file to point the server's hostname to its IP address. The hosts file, /etc/hosts, maps domain names to IP addresses locally on the machine. Open this file with nano or your favorite text editor.
Search for the line that has your server hostname after 127.0.0.1:
/etc/hosts
. . .
# The following lines are desirable for IPv4 capable hosts
127.0.0.1 ipa.example.com ipa.example.com
127.0.0.1 localhost.localdomain localhost
127.0.0.1 localhost4.localdomain4 localhost4
. . .
Change 127.0.01 to your server IPv4 address.
Modified /etc/hosts
. . .
# The following lines are desirable for IPv4 capable hosts
your_server_ipv4 ipa.example.com ipa.example.com
127.0.0.1 localhost.localdomain localhost
127.0.0.1 localhost4.localdomain4 localhost4
. . .
If you have IPv6 enabled you will need to edit the IPv6 mapping as as well, changing the ::1 line with your hostname.
/etc/hosts
...
# The following lines are desirable for IPv6 capable hosts
::1 ipa.example.com ipa.example.com
::1 localhost.localdomain localhost
::1 localhost6.localdomain6 localhost6
...
Change ::1 to your server IPv6 address.
Modified /etc/hosts
...
# The following lines are desirable for IPv6 capable hosts
your_server_ipv6 ipa.example.com ipa.example.com
::1 localhost.localdomain localhost
::1 localhost6.localdomain6 localhost6
...
Save and exit the file.
By default, every time the system boots. CentOS uses the configuration in /etc/cloud/templates/hosts.redhat.tmpl to generate /etc/hosts. To make this configuration change permanent, we will need to make similar changes in that file as well.
Open the file.
# nano /etc/cloud/templates/hosts.redhat.tmpl
Change the 127.0.0.1 ${fqdn} ${hostname} line to use your server IPv4 address.
Modified /etc/cloud/templates/hosts.redhat.tmpl
...
# The following lines are desirable for IPv4 capable hosts
your_server_ipv4 ${fqdn} ${hostname}
127.0.0.1 localhost.localdomain localhost
127.0.0.1 localhost4.localdomain4 localhost4
...
Similarly, change the ::1 ${fqdn} ${hostname} line to use your IPv6 address, if you're using one.
Modified /etc/cloud/templates/hosts.redhat.tmpl
...
# The following lines are desirable for IPv6 capable hosts
your_server_ipv6 ${fqdn} ${hostname}
::1 localhost.localdomain localhost
::1 localhost6.localdomain6 localhost6
...
Exit and save the file.
Next we will configure the random number generators within CentOS. This will allow FreeIPA to preform the cryptographic functions it needs for authentication.
Configuring the Random Number Generator
Setting up FreeIPA requires a lot of random data for the cryptographic operations that it runs. By default, a virtual machine will run out of random data or entropy very quickly. To get around this, we will use rngd, a software random number generator. rngd works by taking data from the hardware devices attached to the server and feeding it into the kernel's random number generator.
First, install rngd.
# yum install rng-tools
Then enable it.
# systemctl start rngd
Make sure the service is automatically started at boot.
# systemctl enable rngd
Finally, verify that rngd is running.
# systemctl status rngd
The output should include active (running) in green.
With all of the dependencies configured and functioning, we can move on to installing the FreeIPA server software itself.
Installing the FreeIPA Server
Now we will be installing ipa-server, the FreeIPA server package itself.
# yum install ipa-server
Then run the FreeIPA installation command. This will run a script that will prompt you for configuration options and install FreeIPA.
# ipa-server-install
In addition to authentication, FreeIPA has the ability to manage DNS records for hosts. This can make provisioning and managing hosts easier. In this tutorial we will not be using FreeIPA's integrated DNS. It is not needed for a basic setup.
Installation script prompt
Do you want to configure integrated DNS (BIND)? [no]: no
Next, you'll need to enter the server's hostname, the domain name, and the Kerberos realm name. Kerberos is an authentication protocol which FreeIPA makes use of behind the scenes for authenticating host machines. It is highly recommended that you use your domain name as the Kerberos realm. Using a different naming scheme will cause problems with FreeIPA's Active Directory integration, and may cause other issues.
Warning: Do not use your root domain (example.com) as your IPA domain name. This can cause DNS issues.
Installation script prompt
Server host name [ipa.example.org]: ipa.example.org
Please confirm the domain name [example.org]: ipa.example.org
Please provide a realm name [EXAMPLE.ORG]: IPA.EXAMPLE.ORG
Next, create a password for the LDAP directory manager. This is needed for FreeIPA's LDAP functionality. Then the IPA admin password, which will be used when logging into FreeIPA as the admin user. Using secure randomly generated passwords here is highly recommended, as your entire system's security depends on them.
Confirm the configuration. After this, the installer will run.
Installation script prompt
Continue to configure the system with these values? [no]: yes
The install process can take several minutes depending on the speed of your server.
Now that we have a completed server installation, we will need to test it.
Verifying the FreeIPA Server Functions
First, verify that the Kerberos realm installed correctly by attempting to initialize a Kerberos token for the admin user.
# kinit admin
If working correctly, this should prompt you for the IPA admin password entered during the install process. Type it in, then press ENTER.
Next, verify that the IPA server is functioning properly.
# ipa user-find admin
This should print out the following:
--------------
1 user matched
--------------
User login: admin
Last name: Administrator
Home directory: /home/admin
Login shell: /bin/bash
Principal alias: admin@IPA.EXAMPLE.COM
UID: 494800000
GID: 494800000
Account disabled: False
----------------------------
Number of entries returned 1
----------------------------
We should also be able to access the web UI at https://ipa.example.com.
Note: The TLS certificate will be untrusted. For now, we'll just bypass the warnings. In the future, you can use your favorite certificate authority to get a valid TLS certificate. Once you have it, you'll need to upload your CA certificate (usually ca.crt), certificate file (your_domain.crt), and key file ( your_domain.key) to the server.
Once you have the files, install the CA using the directory manager password you set earlier. You can precede the command with a space to prevent it from being saved to the shell history.
# ipa-cacert-manage -p your_directory_manager_password -n httpcrt -t C,, install ca.crt
Then install the site certificate and key.
# ipa-server-certinstall -w -d your_domain.key your_domain.crt
You will need to restart your server for these changes to take effect.
In the web UI, log in as the admin user. Username will be admin and Password will be the IPA admin password you set earlier. The top of the page will say Authenticating and then you will be brought to the main IPA page, which looks like this:
Finally, let's explore some of FreeIPA's features by adding a new user.
Configuring IPA Users
FreeIPA has a very extensive set of user management and policy features. Similar to standard Unix users, FreeIPA users can belong to groups. Either groups or individual users can be allowed or denied access to hosts (client machines) or groups of hosts (hostgroups) based on policies. FreeIPA can also manage sudo access; groups or users can be granted sudo access on hosts or host groups.
This guide will just go over how to add new users to get you started.
To add a user, click the Identity tab and click on Users. This will display a table of users. Click the + Add button above the table to add a new user. Fill in the required fields (like first and last name) in the form that opens, then click Add to add the user as is or Add and edit to configure advanced details.
The advanced details can also be accessed by clicking on the user in the original table. This is what an administrator sees when looking at a user's details:
Regular users can also log in to the IPA GUI. They will be able to view their own permissions and edit personal details.
New users will be asked to change their password the first time they log in to an IPA machine. This works in the IPA GUI as well as over SSH. One helpful feature is the ability to add SSH keys. A user can upload their public SSH keys and have them propagate out to the IPA machines, allowing passwordless login. The user can then remove the SSH key at any time without having to worry about it still being present on individual servers.
Conclusion
Since that you have a working FreeIPA server, you will need to
configure clients to authenticate against it. Ubuntu and CentOS both have installer scripts for the FreeIPA client which allows them to be easily provisioned. In addition, FreeIPA is an LDAP server. Any service supporting LDAP authentication can be setup to authenticate against your FreeIPA server.