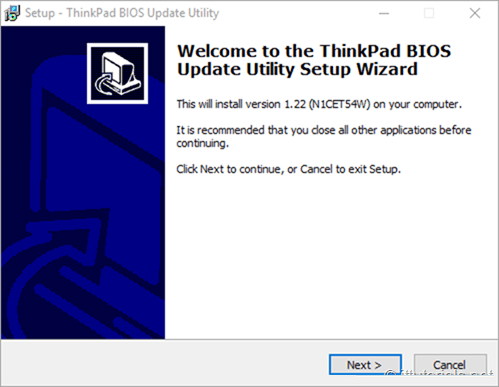
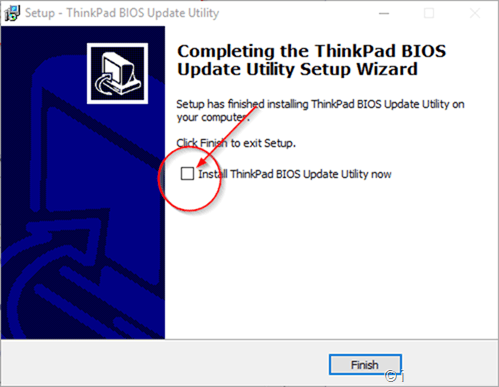
Apple announced a number of new features and changes at WWDC 2017. From improvements to Messages and Apple Pay to powerful multitasking and file management on the iPad, following are the best new features coming in iOS 11.
iMessage Apps Are Easier to Access, and Messages Are Synced Between Devices
The Messages app has a redesigned app drawer to make iMessage apps and stickers more discoverable and easier to use. These apps were added in iOS 10, but were hidden behind a button, which was kind of annoying. The new layout makes things much more accessible.Your messages will now be stored in iCloud, too. All of your conversations will be synchronized between your devices when you sign in with your iCloud account. That way, you can delete a message on one device and it goes away everywhere. Messages remain end-to-end encrypted, even while stored in the cloud.
This also allows Apple to optimize device storage. Since your messages are stored in the cloud, they don’t have to all remain on your device. This means more free space and smaller and faster device backups.

Pay Your Friends Over iMessage with Apple Pay
Apple Pay will now allow person-to-person payments. It’s integrated right into Messages as an iMessage app, making it easy to send money while chatting. Money you receive goes into your Apple Pay cash card and you can send it to someone else, make a purchase with Apple Pay, or transfer it to your bank account.You’ll have to authenticate with Touch ID before sending money, just as you do when making purchases.
It’ll even try to detect when you want to use it. If you receive a message in iMessages saying you owe money, for example, the keyboard will automatically suggest Apple Pay as an option and automatically fill in the amount of money.
Lastly, 50% of US retailers will be accepting Apply Pay in the US by end of 2017, according to Apple.

Siri Gets a More Natural Voice and Other Improvements
Siri’s voice is being upgraded: Apple has used “deep learning” to create a more “natural and expressive” voice. Siri has both a male and female voice, and it can even say the same word in different ways for a more realistic conversation experience.Apple’s virtual assistant is gaining built-in translation features as well. Siri will speak the translation aloud for you, so you know exactly how to pronounce it. It’ll support translation from English to Chinese, French, German, Italian, and Spanish initially.
In addition to suggesting apps, and when you should leave for work based on traffic, Siri will use on-device learning to understand more about topics of interest to you. Siri can suggest news topics you might be interested in, more easily respond with your location in messages, or make calendar events after you book hotel reservations in Safari on the web, for example. The keyboard will learn words you might want to use based on what you read. This is all done on your device, and not in the cloud.
Lastly, developers can now take advantage of SiriKit to integrate Siri with more types of apps, everything from task management to notes to banking. So hopefully, Siri will be able to do more as developers jump on board.

Camera Improvements Mean Videos and Photos Take Up Less Space
iOS 11 will use HEVC video encoding, which means videos you capture are up to two times smaller in storage size. Apple is also switching photo capture from JPEG to HEIF for up to two times better compression as well, so photos you take on your device will use up to two times less space. You can still share those photos with people on other devices.
Improved Memories and Live Photos
The Memories feature in the Photos app can now use machine learning to identify activities like anniversaries, memories of your children, your pets, or sporting events. It uses computer vision to identify photos and automatically pick the best videos and photos. It can also work in portrait mode as well as landscape mode, so you can watch in whatever aspect ratio you prefer.There are improvements for live photos, too. You can now more easily edit live photos, trimming them and marking any frame of the photo as the “key photo” in the live photo. It can also turn a live photo into a seamless loop using computer vision technology.

Control Center Consolidates to One Unified, 3D Touch-Capable Page
The Control Center that appears when you swipe up from the bottom of the screen has been redesigned. It’s now a single page that includes all the features—You don’t need to swipe left and right to use them (which is sure to be less confusing for many people).In addition, you can now 3D touch an option to access more controls. For example, you can 3D touch the music control to see more information and playback controls.

The Lock Screen and Notification Center Have Been Combined
The lock screen and notification center are now the same screen. When you swipe down from the top of the screen, you’ll see all your notifications. You can still swipe to the left to access your widgets or the right to access your camera.The lock screen and notification center are now the same screen. When you swipe down from the top of the screen, you’ll see all your notifications. You can still swipe to the left to access your widgets or the right to access your camera.
Apple Maps Improves Navigation and Adds Indoor Maps
Apple Maps is, once again, improving navigation a little bit. Apple Maps will display the speed limit and provide lane guidance to guide you into the appropriate lane while navigating.In addition, Maps is getting indoor maps of malls and airports, with directories and a search feature. Apple is beginning with many malls and airports, but will be adding more as time goes on.

Do Not Disturb Will Auto-Enable While Driving
iOS 11 includes a new “Do Not Disturb While Driving” feature that uses Bluetooth or Wi-Fi to determine whether you’re driving. It will automatically hide your notifications if you are (though you can tell the iPhone you’re not driving if you want notifications to show up).The Messages app can even automatically auto-respond to people who text you, saying that you’re driving and can’t respond right now. They can text you to say it’s urgent if they need you to respond as soon as possible.

AirPlay 2 Becomes Part of HomeKit, and Brings Multi-Room Audio
HomeKit will now support speakers, so you can configure and control your speakers alongside your other smarthome devices. Apple has a new AirPlay 2 protocol that enables multi-room audio, too. You can finally play music to different speakers throughout your home from apps in iOS—no need for iTunes on the desktop.You can now also play audio to your Apple TV from your iOS device or Mac, enabling those speakers connected to your media center to become AirPlay speakers.

Apple Music Gets Some Social Improvements
Apple Music will now show you what your friends are listening to, so you can more easily discover new music you might want to listen to. You can create a profile, make it public or private, and follow people with similar taste.Developers will have a MusicKit for Apple Music API they can use to gain full access to Apple Music, too. For example, Shazam can automatically add songs it identifies to your Apple Music collection, and DJ apps can provide access to the entire Apple Music library.

The App Store Has Been Redesigned
The App Store is being completely redesigned to make it easier to discover new apps and games. Launch it and you’ll see a new “Today” tab that provides better app discovery. Every day there’s a new app of the day and game of the day, and you might also see how-to guides with information about apps you already use on the Today tab. You can scroll down to see older information from previous days, too.At the bottom of the page, you’ll see that apps are now sorted into both “Games” and “Apps”, so you can easily browse either games or apps that aren’t games.

Apple Has Improved Many iOS Core Technologies
Alongside the improved Metal 2 graphics API and HEVC video encoding technology, iOS will gain machine learning and augmented reality features for developers to build on.iOS is also making machine learning easier for developers to use with Core ML. There’s a vision API that provides developers with an easier way to recognize faces and landmarks, for example. There’s also a natural language API for understanding text. Again, this all happens on the device, not in the cloud.
Augmented reality (AR) features will be easier for developers to use. ARKit will make it easier for developers to make augmented reality features in their apps—Pokémon Go used AR to show Pokemon superimposed over a video of the real world, for example. Apple showed off an improved Pokémon Go app that showed Pokéballs bouncing more realistically over the ground.
Apple also demonstrated a developer app that allowed you to add virtual objects to a table. The app used surface detection to place the objects. Apple says this will make iPhones and iPads “the largest AR platform in the world” overnight.

The iPad Gets new Multitasking Features
There are a lot of new features in iOS 11 that make iPads more powerful. The dock at the bottom of the screen can contain many more apps, and you can now swipe up from the bottom of the screen in any app to more easily switch between apps. You can drag an app icon from the dock and position it on your screen to easily start multitasking. There’s also a new app switcher.iPads will now support drag-and-drop for text, images, and links between apps. You can select multiple things and drag them, too. You can drag in the multitasking interface, or drag content from the dock.
In addition, the iPad’s keyboard allows you to flick on keys to access punctuation and numbers, making typing faster.

A File Management App Finally Comes to the iPad
There’s a new Files app for iPad that supports nested folders, list view, favorite, search, tags, and recent files. It supports not only iCloud, but also third-party storage providers like Dropbox, OneDrive, and Google Drive. When you search or view recent files, you’ll see all your files in one place.You can drag-and-drop email attachments to the Files app to save them, for example. Or you can tap and hold on the Files app on the dock and then drag and drop files from the Files app into any other app.
Apple didn’t say this app wouldn’t appear on iPhone, but it was strongly implied that this app will only be for the iPad.

The iPad Gets More Markup Features for the Apple Pencil
Apple is offering more markup features throughout iOS 11, making the Apple Pencil more useful. When you take a screenshot, you can tap a thumbnail that appears and use an Apple Pencil to mark up and draw on those screenshots. Anything you mark up can be saved as a PDF. You can draw in emails, too.Your handwritten text is now searchable, thanks to machine learning detecting what you’re writing—so you can find handwritten notes with Spotlight search.
Notes now includes a built-in document scanner that can scan paper notes. You can then mark them up with your pencil, so it’s a convenient way to digitally fill out paper forms. You can draw even in notes you’re typing in Apple Note, too.

Many More Features
Apple also mentioned a few features targeted at users in China, including a QR code reader application integrated into the main Camera app and integrated on the lock screen.There are many other features Apple didn’t mention, too. The above slide reveals that it will contain a one-handed keyboard, Wi-Fi password sharing, screen recording, flight status information in Spotlight, and lots more.