
In my previous article, we set up redundant OpenDNS Umbrella virtual appliances to forward DNS data from our internal network to OpenDNS. We concluded with reports that correctly display IP addresses from our internal network. Now we want to go further and record Active Directory information such as computer login and group information.
To do this, we’ll need to create an OpenDNS service user account on our domain, set up our domain controllers with the OpenDNS Connector service, and run a configuration script against all of our domain controllers. The connector will watch our domain controllers that the configuration script has modified and will relay the information to our OpenDNS Umbrella account.
Download required files
To get started, first download the Sites and Active Directory components from OpenDNS Umbrella > Configuration > System Settings > Sites & Active Directory > Download Components:
Download AD components
Download the files for the Windows Configuration and the Windows Service.
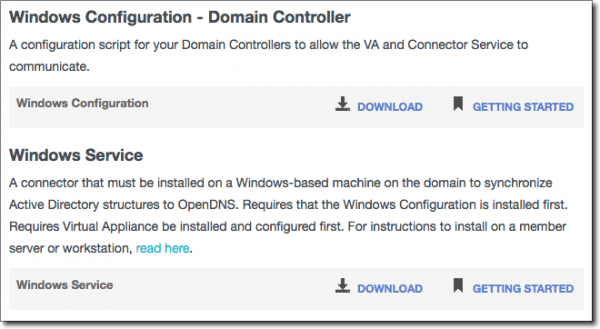
AD service and configuration script download
When finished downloading, you’ll have three files: OpenDNS-WindowsConfigurationScript-20130627.wsf, Config.dat, and Setup.msi. The Config.dat file will contain your OpenDNS account identity information.
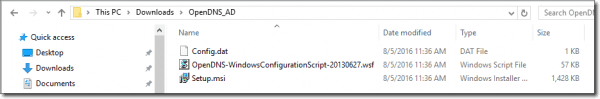
AD Connector files
Create optional new domain controller
You have the option to keep the connector service separate from your domain controllers by using a member server. The minimum specs are similar to those for the OpenDNS Virtual Appliances and are as follows:- Static IP address
- 4 CPU cores and 1.5GB RAM
- 7GB of disk space
- The following open outbound ports: 53 TCP & UDP, 443 TCP & UDP, 80 TCP, 2222 TCP, 123 UDP, and 53 UDP
- White-list the processes OpenDNSAuditClient.exe and OpenDNSAuditService.exe if local anti-virus software is installed
If you create a new member server, be sure to open WMI ports in the firewall with the following command run as Administrator:
netsh advfirewall firewall set rule group=”Windows Management Instrumentation (WMI)” new enable=yes
Create an OpenDNS service user
In addition to the connector and scripts, we need to create a new service user on our domain so our services run uninterrupted. Create a new domain user account and set the logon name to OpenDNS_Connector.Provide a strong password and then check the Password Never Expires checkbox. Add the new user to the following groups:
- Event Log Readers
- Distributed COM users
- Enterprise Read-only domain controllers (RDOC)
Set up domain controllers with cscript
Next we want to run the .wsf script against all of our domain controllers. Open and run an elevated command prompt as Administrator.According to the instructions here (OpenDNS Umbrella account required), from the command prompt, enter c:\>cscript<filename> where <filename> is the name of the configuration script you downloaded. The script will display your current configuration, then offer to auto-configure the domain controller for operation y/n. Type y to continue. If the auto-configure steps are successful, the script will register the domain controller with the Umbrella Dashboard.
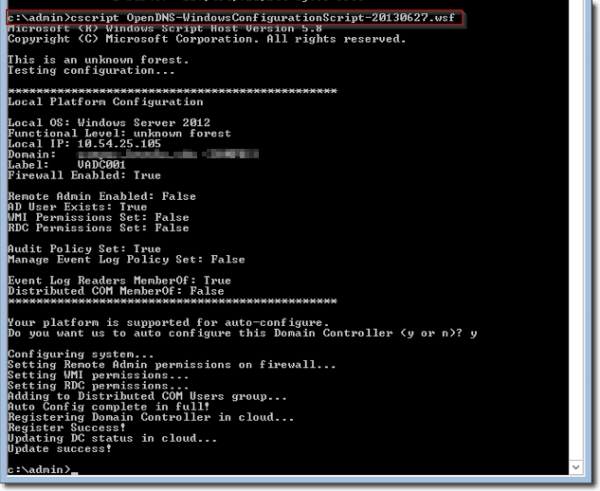
Cscript on domain controller
Again, be sure to run the .wsf visual basic script on all of your domain controllers in each of your sites. In this instance, I only was required to run the .wsf script against one domain controller.
Install the connector
If you have a domain controller that is a Core 2012 R2 server, simply copy the files to the c:\ drive, then run the Setup.msi file from the default command prompt with the command: c:\>.\Setup.msi.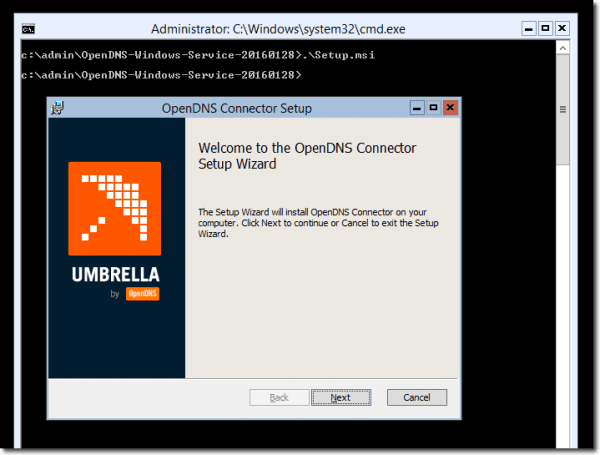
OpenDNS Connector setup
When prompted, provide the password for the OpenDNS Connector service account that we created earlier.

OpenDNS service account credentials
After we’ve verified authentication, we can jump onto our OpenDNS dashboard and confirm that our AD Connector is listed, which we can see in the following screenshot.
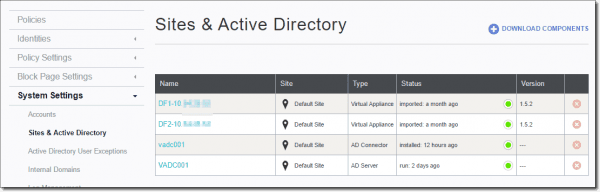
AD Connector established
Testing AD integration
Once our AD Connector and AD Servers are reporting to our OpenDNS Umbrella account, we can now see our AD User and Group information listed in the reports under the Identity column.
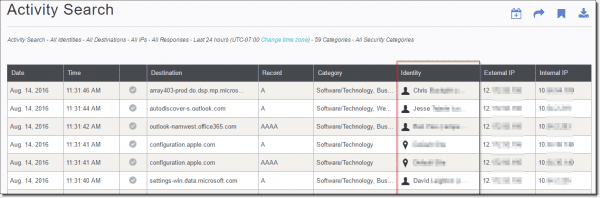
Activity displays identity information
Conclusion
With just a little extra work, we can extend the amount of information available to us on our OpenDNS Umbrella Reporting console to include Active Directory information. If your organization has multiple sites, you can set up Connectors to monitor each location concurrently at no additional cost. It’s nice that OpenDNS Umbrella provides the support and tools necessary to secure and categorize DNS, provide accurate reporting, and manage DNS traffic from a single web-based console.