In the previous part of this article series, we created our first security policy. In this final part, it is time to start enrolling mobile devices.
If you would like to read the other parts in this article series please go to:
Figure 1
When they try to login, the OneDrive app detects the account is an Office 365 account (and therefore it is OneDrive for Business), and takes the user to the Office 365 portal to complete the sign in process:
Figure 2
Once the user types his username, he is asked to enroll the device (because of the policy we created earlier requiring devices to enroll in order to access Office 365 data):
Figure 3
When the user clicks Enroll, he is asked to install the Microsoft Intune Company Portal app:
Figure 4
By clicking on the iTunes store link, the user is taken to the Apple store to download the app:
Figure 5
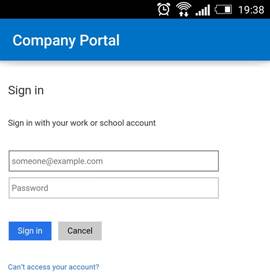
Once installed, the user opens the Company Portal app, types his credentials and clicks on Sign in:
Figure 6
The app verifies the user credentials and tries to log the user into Intune. Once in, the user is taken through the process of enrolling the device. He clicks on Enroll:
Figure 7
A webpage opens showing the device is being enrolled:
Figure 8
The user is then taken to Settings where he needs to install a new (organization’s) Management Profile:
Figure 9
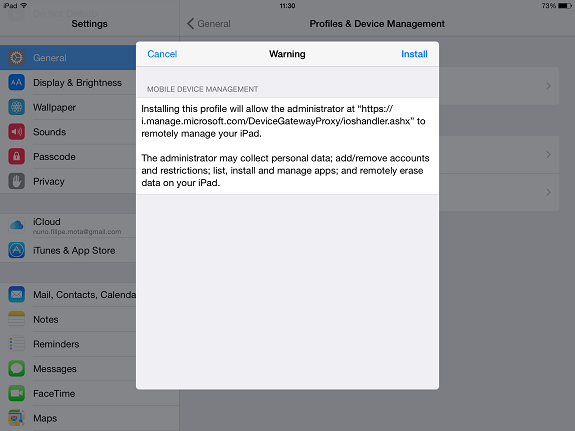
The warning lets the user know what this management profile will allow administrators (MDM) to do on the device:
Figure 10
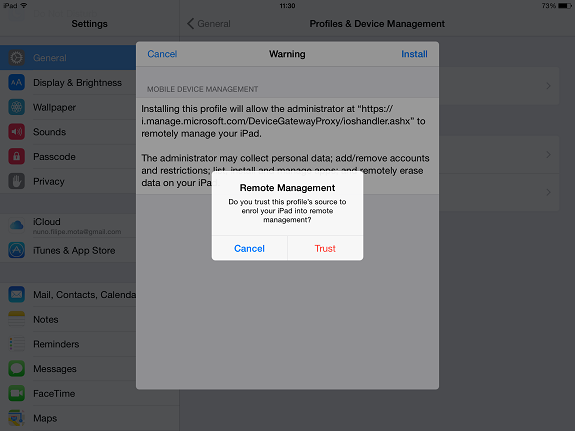
The user clicks on Trust:
Figure 11
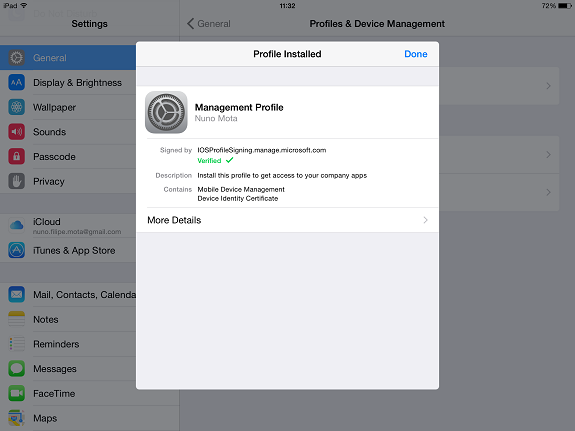
And once the process is completed, the user clicks on Done:
Figure 12
If the device’s password does not meet the requirements set by the security policy, the user is prompted to create a device passcode:
Figure 13
The user is then taken back to the Company Portal app with a notification stating that the device has been enrolled successfully and that he can shortly access Office 365 data:
Figure 14
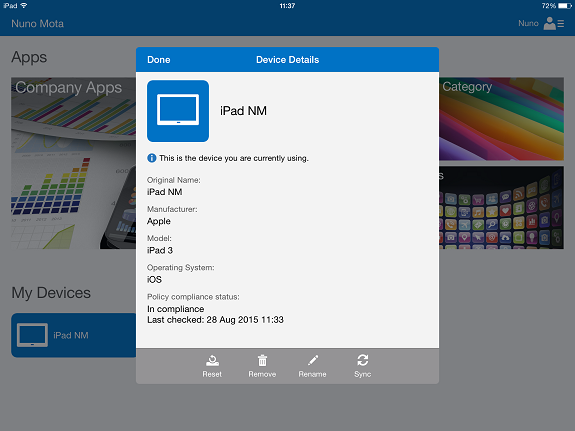
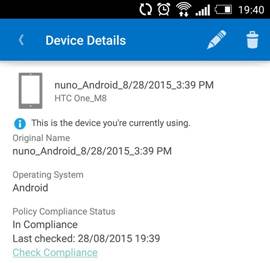
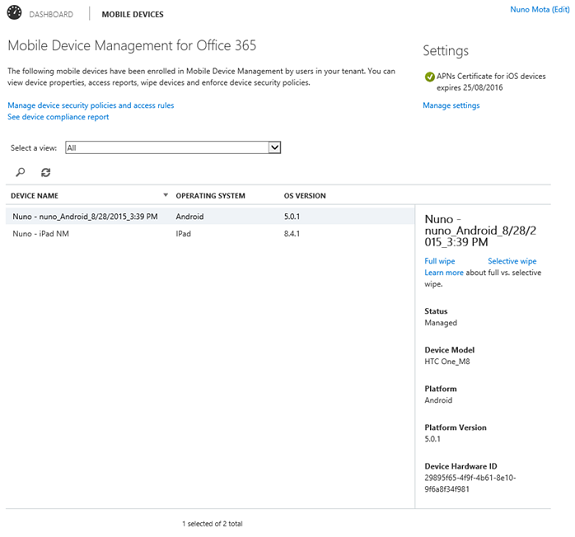
By clicking on the device, we can see further details around the model, operating system and when the device was last checked for compliance:
Figure 15
As we saw, the entire process is straightforward, not leaving much room for user error, and pretty much identical to when we enrolled a device in Intune in my last article series.
If we chose to manage iOS email profiles with a security profile (which is required so an admin can wipe a device, for example), the next step is to delete any work or school email accounts. MDM for Office 365 will recreate the email account for the user, and then MDM manages the account and a remote device wipe will work.
Figure 16
This email explains why only this email is visible and exactly what the user needs to do in order to be able to access Office 365:
Figure 17
When the user clicks on the Enroll your device link, he/she is taken to a webpage to start the enrollment process:
Figure 18
From this webpage, a link guides the user to the Google Play store in order to download the Intune Company Portal app:
Figure 19
Once the app is installed, the user needs to sign in to Office 365 with his/hers credentials:
Figure 20
Step by step the user is guided through the process of enrolling the device:
Figure 21
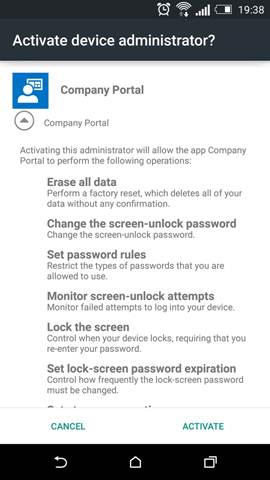
A detailed list of what MDM can do on the device is displayed that the user has to agree to:
Figure 22
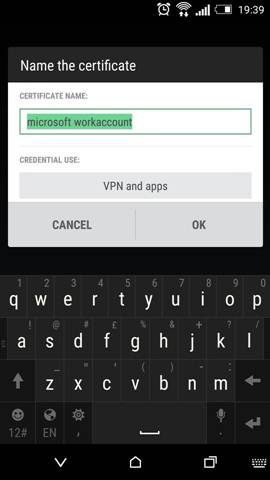
After clicking ACTIVATE a digital certificate needs to be installed for MDM to securely communicate with and manage the device:
Figure 23
The enrollment process is finally complete:
Figure 24
Through the company portal, the user can check the applications made available through the company app store (none in this case):
Figure 25
As well as a list of the devices the user has already enrolled:
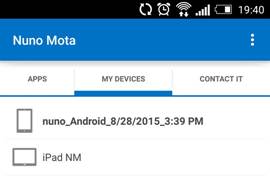
Figure 26
Selecting a device will list additional information regarding the device itself:
Figure 27
Now that the device has been enrolled and it is in compliance with the security policy we created, the user is given access to his entire mailbox:
Figure 28
Figure 29
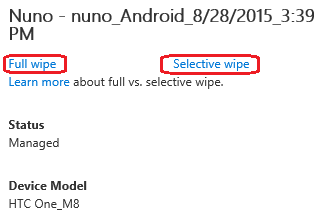
From here we can, for example, perform a full wipe or a selective wipe.
Figure 30
If we select selective wipe, the following warning message is displayed:
Figure 31
If we select full wipe instead, the following warning message is displayed:
Figure 32
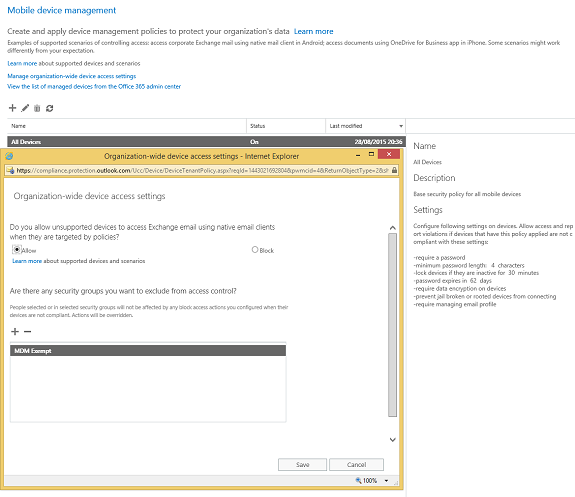
If we want to block unsupported devices from accessing Exchange email using Exchange ActiveSync we go to the Compliance Center, select Device management and then click on Manage organization-wide device access settings:
Figure 33
In order to unblock noncompliant or unsupported device for a user or group of users, we have several options:
Figure 34
We can filter the above report by operating system or by status:
Figure 35
If you would like to read the other parts in this article series please go to:
If you would like to read the other parts in this article series please go to:
- Mobile Device Management in Exchange Online (Part 1)
- Mobile Device Management in Exchange Online (Part 2)
4: Enroll Users
After we have deployed a mobile device management policy, each licensed Office 365 user in the organization that the device policy applies to will receive an enrollment message the next time they sign into Office 365 from their mobile device. That could be when they try to login to the portal, to an Office app like Word or OneDrive, or create an email profile for example. They must complete the enrollment and activation steps before they can access Office 365 email and documents.
When users enroll their device in Mobile Device Management (MDM) for Office 365, they might be required to set up a password, together with allowing the option for the work organization to wipe the device. A device wipe can be performed, for example, to remove all data from the device if the password is entered incorrectly too many times or if usage terms are broken.
MDM for Office 365 works with most but not all mobile devices. The following are the supported ones at the time of writing this article:
- iOS 7.1 or later;
- Android 4 or later;
- Windows 8.1 (phone or tablet).
iPad
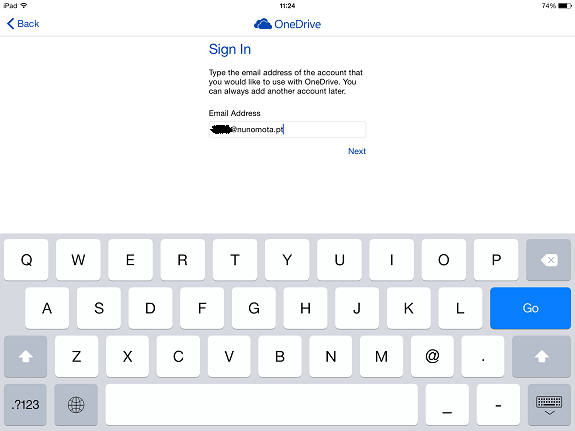
Let us look at the example of a user that tries to configure their OneDrive on an iPad:Figure 1
When they try to login, the OneDrive app detects the account is an Office 365 account (and therefore it is OneDrive for Business), and takes the user to the Office 365 portal to complete the sign in process:
Figure 2
Once the user types his username, he is asked to enroll the device (because of the policy we created earlier requiring devices to enroll in order to access Office 365 data):
Figure 3
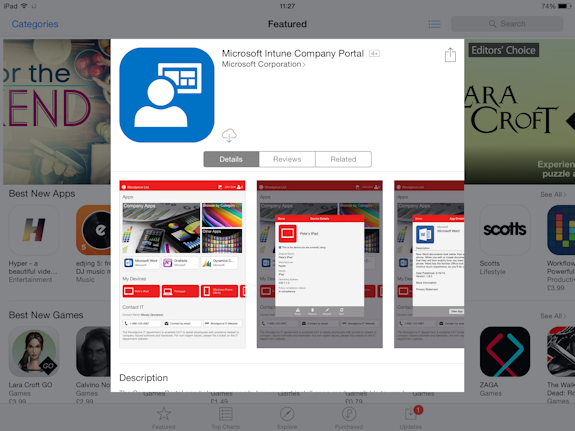
When the user clicks Enroll, he is asked to install the Microsoft Intune Company Portal app:
Figure 4
By clicking on the iTunes store link, the user is taken to the Apple store to download the app:
Figure 5
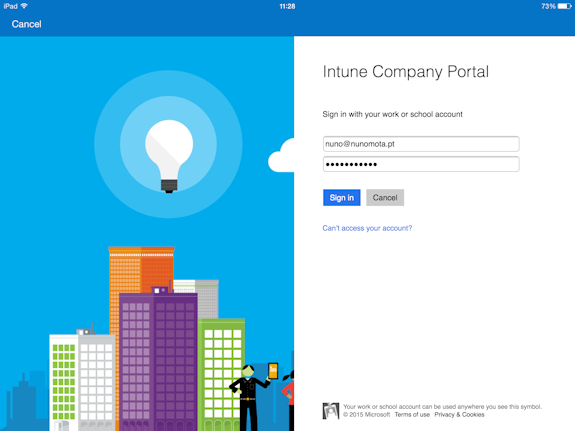
Once installed, the user opens the Company Portal app, types his credentials and clicks on Sign in:
Figure 6
The app verifies the user credentials and tries to log the user into Intune. Once in, the user is taken through the process of enrolling the device. He clicks on Enroll:
Figure 7
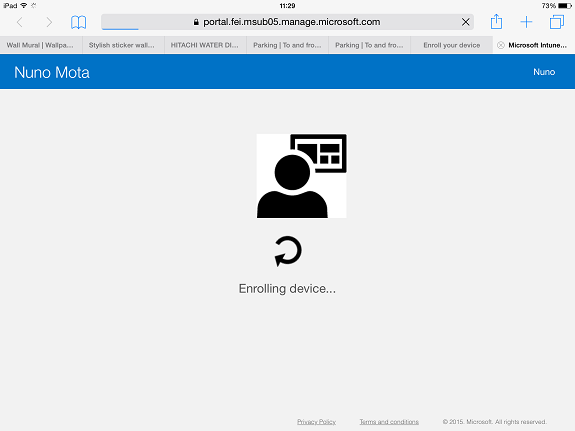
A webpage opens showing the device is being enrolled:
Figure 8
The user is then taken to Settings where he needs to install a new (organization’s) Management Profile:
Figure 9
The warning lets the user know what this management profile will allow administrators (MDM) to do on the device:
Figure 10
The user clicks on Trust:
Figure 11
And once the process is completed, the user clicks on Done:
Figure 12
If the device’s password does not meet the requirements set by the security policy, the user is prompted to create a device passcode:
Figure 13
The user is then taken back to the Company Portal app with a notification stating that the device has been enrolled successfully and that he can shortly access Office 365 data:
Figure 14
By clicking on the device, we can see further details around the model, operating system and when the device was last checked for compliance:
Figure 15
As we saw, the entire process is straightforward, not leaving much room for user error, and pretty much identical to when we enrolled a device in Intune in my last article series.
If we chose to manage iOS email profiles with a security profile (which is required so an admin can wipe a device, for example), the next step is to delete any work or school email accounts. MDM for Office 365 will recreate the email account for the user, and then MDM manages the account and a remote device wipe will work.
Android HTC
Let us now go through the same process but for an Android device. In this example, the user configured an email account when MDM was already being enforced. As such, once the user opens the mailbox, only one email from MDM is visible:Figure 16
This email explains why only this email is visible and exactly what the user needs to do in order to be able to access Office 365:
Figure 17
When the user clicks on the Enroll your device link, he/she is taken to a webpage to start the enrollment process:
Figure 18
From this webpage, a link guides the user to the Google Play store in order to download the Intune Company Portal app:
Figure 19
Once the app is installed, the user needs to sign in to Office 365 with his/hers credentials:
Figure 20
Step by step the user is guided through the process of enrolling the device:
Figure 21
A detailed list of what MDM can do on the device is displayed that the user has to agree to:
Figure 22
After clicking ACTIVATE a digital certificate needs to be installed for MDM to securely communicate with and manage the device:
Figure 23
The enrollment process is finally complete:
Figure 24
Through the company portal, the user can check the applications made available through the company app store (none in this case):
Figure 25
As well as a list of the devices the user has already enrolled:
Figure 26
Selecting a device will list additional information regarding the device itself:
Figure 27
Now that the device has been enrolled and it is in compliance with the security policy we created, the user is given access to his entire mailbox:
Figure 28
5: Manage Devices
Once we have one or more devices enrolled, they will show up in the MDM page:Figure 29
From here we can, for example, perform a full wipe or a selective wipe.
Figure 30
If we select selective wipe, the following warning message is displayed:
Figure 31
If we select full wipe instead, the following warning message is displayed:
Figure 32
If we want to block unsupported devices from accessing Exchange email using Exchange ActiveSync we go to the Compliance Center, select Device management and then click on Manage organization-wide device access settings:
Figure 33
In order to unblock noncompliant or unsupported device for a user or group of users, we have several options:
- Remove the user or users from the security group the policy has been applied to (Office 365 admin center> Groups, and then select group name. Click Edit members);
- Remove the security group the users are a member of from the device policy (Compliance Center> Device management, and then select the device policy name. Click Edit > Deployment);
- Unblock all noncompliant devices for a device policy. Go to Compliance Center> Device management, and then select device policy name. Click Edit > Access requirements. Select Allow access and report violation).
Figure 34
We can filter the above report by operating system or by status:
Figure 35
Conclusion
The built-in Mobile Device Management solution in Office 365 is a great addition to the Office 365 family as not every organization requires all the features that Intune provides, has the in-house expertise to deploy and manage it, or is able to justify its cost. MDM for Office 365 It is a “simplified version” of Intune that helps organizations secure and manage their mobile devices. We can create MDM policies with settings that can help control access to the organization’s Office 365 email and documents for supported mobile devices and apps. If a device ever gets lost or stolen, we can remotely wipe the device to remove sensitive organizational information.
- Mobile Device Management in Exchange Online (Part 1)
- Mobile Device Management in Exchange Online (Part 2)