In the previous part of this article series we presented the new built-in Mobile Device Management (MDM) solution in Office 365, what it can be used for and we started configuring it. Now we will create our first security policy.
If you would like to read the other parts in this article series please go to:
Please note that the policies and access rules we create in MDM override the Exchange ActiveSync mobile device mailbox policies and device access rules created in the Exchange Admin Center. After a device is enrolled in MDM, any Exchange ActiveSync mobile device mailbox policy or device access rule applied to the device is simply ignored.
If we create a policy to block access based on certain settings being enabled or not, users will be blocked from accessing Office 365 resources when using a supported app. The settings that can block users from accessing Office 365 resources are in the following categories:
Figure 1
Before creating our first security policy, let us have a quick look at the settings we can use to help us secure and manage mobile devices.
Security settings
Encryption settings
Jail broken setting
Managed email profile option
This option can block users from accessing their Office 365 email if they are using a manually created email profile. Users on iOS devices must delete their manually created email profile before they can access their email. After they delete the profile, a new profile will be automatically created on the device.
Cloud settings
System settings
Application settings
Device capabilities settings
Remote wipe
If a device is lost or stolen, we can remove organizational data and help prevent access to Office 365 resources by performing a wipe from Office 365 admin center>Mobile device management. As we will see later in this article series, we can perform a selective wipe to remove only organizational data or a full wipe to delete all information from a device and restore it to its factory settings.
Let us now start creating our new policy. When creating a new policy, we can set it to allow access and report policy violation where a user's device is not compliant with the policy. This way we can see how many mobile devices would be impacted by the policy without actually blocking them.
Back in the Mobile device management page, we can see the details of our new security policy including that it is still being created:
Figure 9
Once it is ready to be used, the Status changes to On:
Figure 10
To help further secure our information, we can block Exchange ActiveSync app access to Office 365 email for mobile devices that are not supported by MDM. To do this:
When we delete a policy or remove a user from a group to which the policy was deployed to, the policy settings, Office 365 email profile and cached emails may be removed from the user's device:
*If the policy was deployed with the option require managing email profile selected (as we did above), then the managed email profile and cached emails in that profile will be deleted from the user's device.
Each user that the removed policy applied to will have the policy removed from their device the next time their mobile device checks in with MDM. If we deploy a new policy that applies to these users' devices, they will be prompted to re-enroll in MDM.
If you would like to read the other parts in this article series please go to:
If you would like to read the other parts in this article series please go to:
- Mobile Device Management in Exchange Online (Part 1)
- Mobile Device Management in Exchange Online (Part 3)
3: Configure Security Policies
Before we start enrolling users’ devices, we need to create one or more Security Policies to enforce users to enroll their devices so we can manage them and protect our organizational data. For example, to help prevent data loss if a user loses their device, we can create a policy to lock devices after 5 minutes of inactivity and have devices wiped after 3 sign-in failures.Please note that the policies and access rules we create in MDM override the Exchange ActiveSync mobile device mailbox policies and device access rules created in the Exchange Admin Center. After a device is enrolled in MDM, any Exchange ActiveSync mobile device mailbox policy or device access rule applied to the device is simply ignored.
If we create a policy to block access based on certain settings being enabled or not, users will be blocked from accessing Office 365 resources when using a supported app. The settings that can block users from accessing Office 365 resources are in the following categories:
- Security;
- Encryption;
- Jail broken;
- Managed email profile.
Figure 1
Before creating our first security policy, let us have a quick look at the settings we can use to help us secure and manage mobile devices.
Security settings
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Require a password | ✔ | ✔ | ✔ |
| Prevent simple password | ✔ | ✔ | ✖ |
| Require an alphanumeric password | ✔ | ✔ | ✖ |
| Minimum password length | ✔ | ✔ | ✔ |
| Number of sign-in failures before device is wiped | ✔ | ✔ | ✔ |
| Minutes of inactivity before device is locked | ✔ | ✔ | ✔ |
| Password expiration (days) | ✔ | ✔ | ✔ |
| Remember password history and prevent reuse | ✔ | ✔ | ✔ |
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Require data encryption on devices | Windows Phone 8.1 is already encrypted and cannot be unencrypted | ✖ | ✔ |
Jail broken setting
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Device cannot be jail broken or rooted | ✖ | ✔ | ✔ |
Managed email profile option
This option can block users from accessing their Office 365 email if they are using a manually created email profile. Users on iOS devices must delete their manually created email profile before they can access their email. After they delete the profile, a new profile will be automatically created on the device.
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Email profile is managed | ✖ | ✔ | ✖ |
Cloud settings
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Require encrypted backup | ✖ | ✔ | ✖ |
| Block cloud backup | ✖ | ✔ | ✖ |
| Block document synchronization | ✖ | ✔ | ✖ |
| Block photo synchronization | ✖ | ✔ | ✖ |
System settings
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Block screen capture | ✔ | ✔ | ✔ (Samsung Knox only) |
| Block sending diagnostic data from device | ✔ | ✔ | ✖ |
Application settings
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Block video conferences on device | ✖ | ✔ | ✖ |
| Block access to application store | ✔ | ✔ | ✖ |
| Require password when accessing application store | ✖ | ✔ | ✖ |
Device capabilities settings
| Setting name | Windows Phone 8.1 | iOS 7.1+ | Android 4+ |
| Block connection with removable storage | ✔ | ✖ | ✖ |
| Block Bluetooth connection | ✔ | ✖ | ✖ |
Remote wipe
If a device is lost or stolen, we can remove organizational data and help prevent access to Office 365 resources by performing a wipe from Office 365 admin center>Mobile device management. As we will see later in this article series, we can perform a selective wipe to remove only organizational data or a full wipe to delete all information from a device and restore it to its factory settings.
Let us now start creating our new policy. When creating a new policy, we can set it to allow access and report policy violation where a user's device is not compliant with the policy. This way we can see how many mobile devices would be impacted by the policy without actually blocking them.
- In Office 365, go to Compliance Center -> Device management:
- Select Add +;
- Enter a Name and Description for the new policy, and select Next:
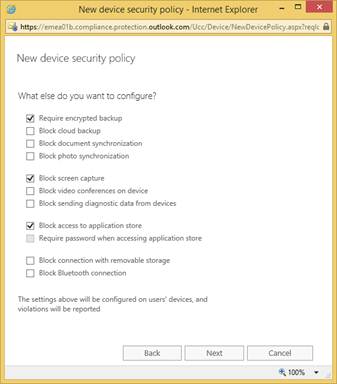
- Select the requirements you want applied to mobile devices in the organization. Notice the last option to allow the device access to Office 365 and report the violation:
- Select any other configurations you want to apply to mobile devices, and select Next:
- Select Apply it to one or more security groups:
- Select Add ;
- Enter a security group name that has members who will test the policy before you deploy it to your organization. The list is empty until we type a security group name, or part of a name, and then click the search icon. Alternatively we can type * and then click the search icon to see a list of all the groups. Select the name, and select Add:
- Select Ok, and then Next.
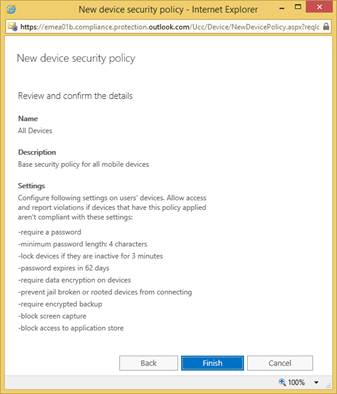
- Review and confirm the details of the new device policy, and select Finish.
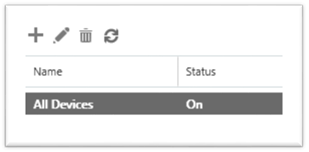
Back in the Mobile device management page, we can see the details of our new security policy including that it is still being created:
Figure 9
Once it is ready to be used, the Status changes to On:
Figure 10
To help further secure our information, we can block Exchange ActiveSync app access to Office 365 email for mobile devices that are not supported by MDM. To do this:
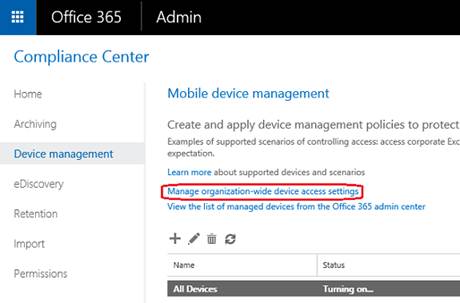
- In the Compliance Center, go to Device management;
- Select Manage organization-wide device access settings:
- Select Block:
- Select Save.
- In the Compliance Center, go to Device management;
- Select Manage organization-wide device access settings:
- Select Add to add the security group that contains users we want to be exclude from being blocked access to Office 365. When a user has been added to this list, they will be able to access Office 365 email when using an unsupported device;
- Enter the security group;
- Select the name, and select Add.
- Select Ok and then Save.
When we delete a policy or remove a user from a group to which the policy was deployed to, the policy settings, Office 365 email profile and cached emails may be removed from the user's device:
| What's removed | Windows Phone 8.1 | iOS 6+ | Android 4+ |
| Managed email profiles* | ✖ | ✔ | ✖ |
| Policy settings | ✔ Except for Block sending diagnostic data from device. | ✔ | ✖ |
*If the policy was deployed with the option require managing email profile selected (as we did above), then the managed email profile and cached emails in that profile will be deleted from the user's device.
Each user that the removed policy applied to will have the policy removed from their device the next time their mobile device checks in with MDM. If we deploy a new policy that applies to these users' devices, they will be prompted to re-enroll in MDM.
Conclusion
In this article we created our first security policy. In the next part we will start enrolling mobile devices.If you would like to read the other parts in this article series please go to:
- Mobile Device Management in Exchange Online (Part 1)
- Mobile Device Management in Exchange Online (Part 3)