
This article will guide you through the steps to set up VPN Server on Windows Server 2016.
VPN server leveraging IPsec Tunnel Mode with Internet Key Exchange version 2 (IKEv2) with the functionality provided by the IKEv2 Mobility and Multihoming protocol (MOBIKE). This tunneling protocol offers inherent advantages in scenarios where the client moves from one IP network to another (for example, from WLAN to WWAN).
The scenario permits a user with an active IKEv2 VPN tunnel to disconnect a laptop from a wired connection, walk down the hall to a conference room, connect to a wireless network, and have the IKEv2 VPN tunnel automatically reconnected with no noticeable interruption to the user.
Installing Certificates on VPN Server and VPN Client
First you need to create certificate templates. Open up Certification Authority Console and from CA console, right click Certificate Templates > Manage > Right Click IPSec > Duplicate template
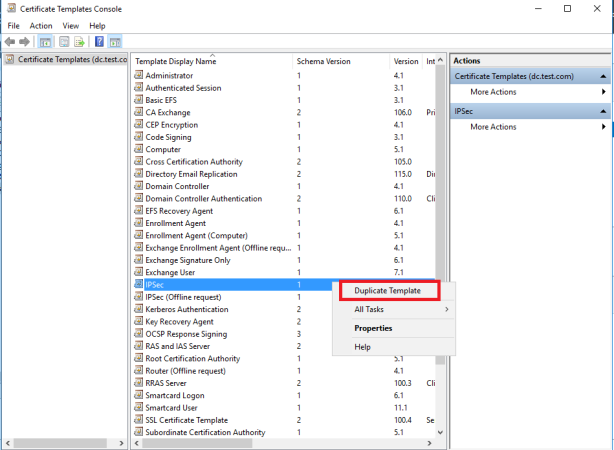
On Request Handling tab click Allow private key to be exported
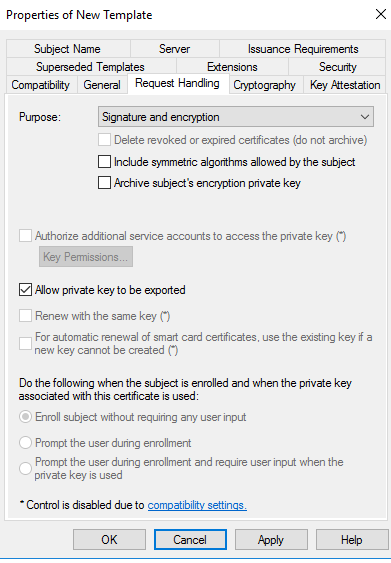
Click Extension tab > Application Policies> Edit
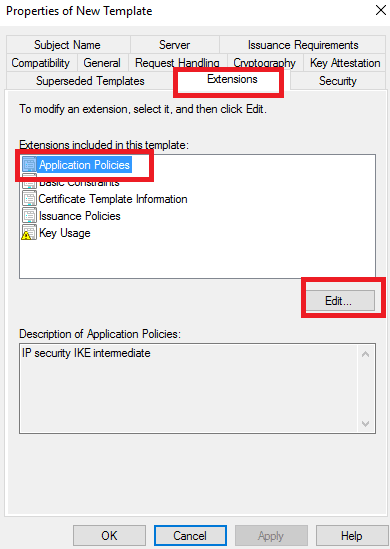
Remove IP Security IKE intermediate > then click Add
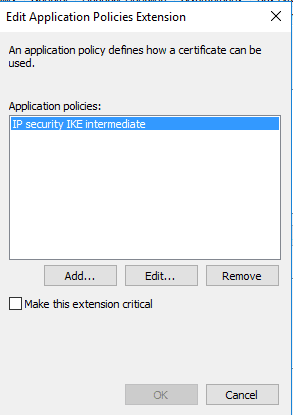
and choose Server Authentication > OK
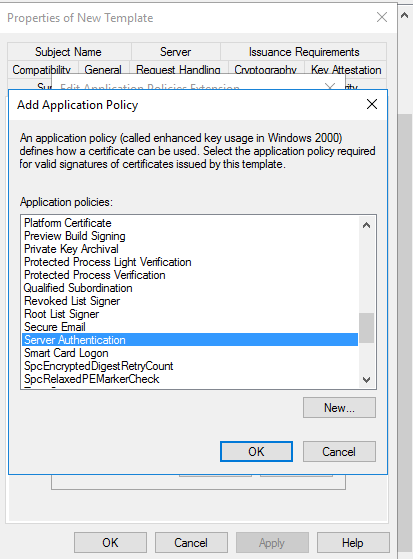
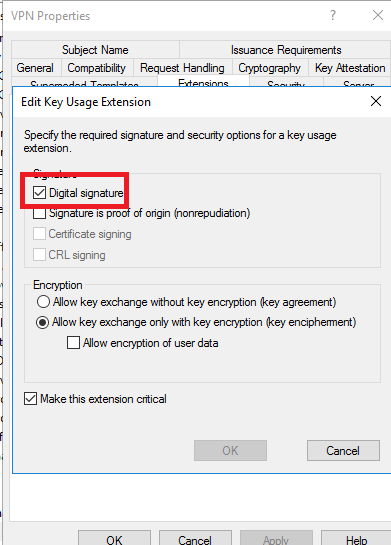
Click Key Usage > Edit

Make sure that Digital signature is selected. If it is, click Cancel. If it is not, select it, and then click OK.
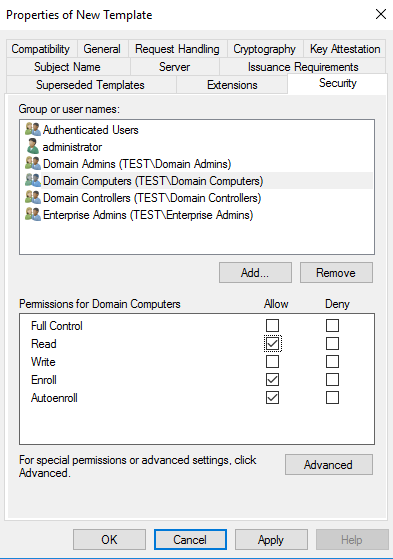
In the Security tab click Object Types> Computers> Add Domain Computers

Make sure Read, Enroll and Autoenroll is selected
In General tab provide a name to template

Now, right click Certification Template> New> Certificate Template to Issue

Choose newly created template, click OK
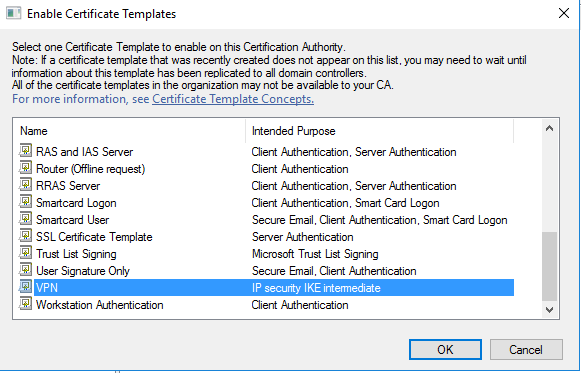
Enrolling Certificate on VPN Server
Now, on your VPN Server, open up Run and type mmc> Add/remove snap-in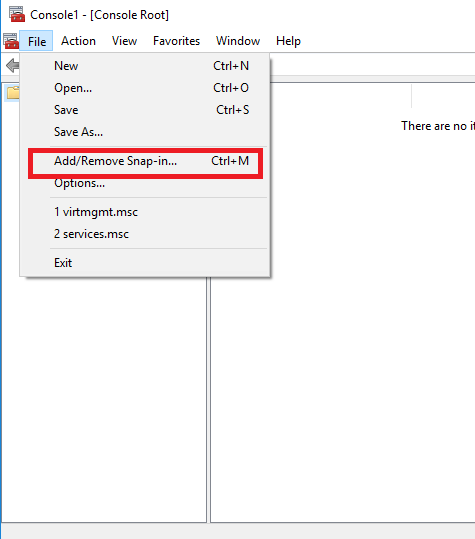
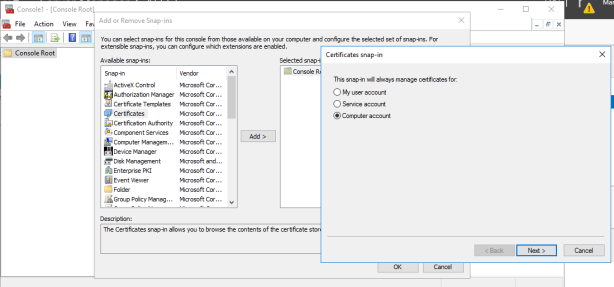
Click Certificates> Add> Computer Account
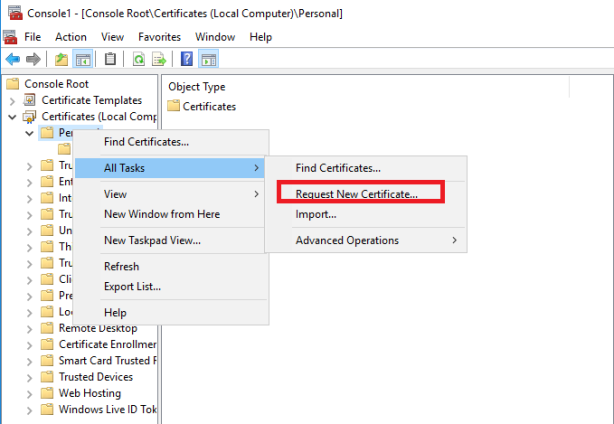
Right click Personal> All tasks> Request New Certificate
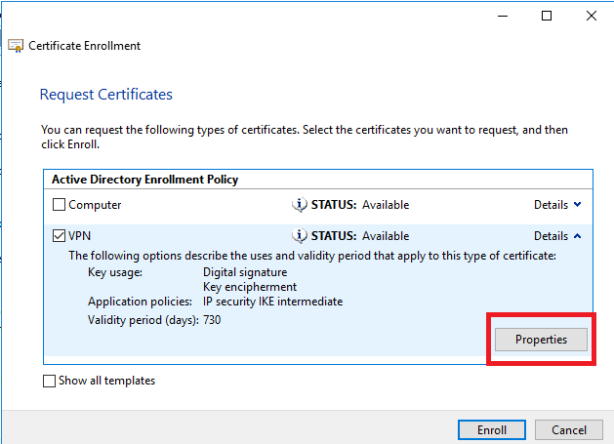
Check Certificate templates > Properties
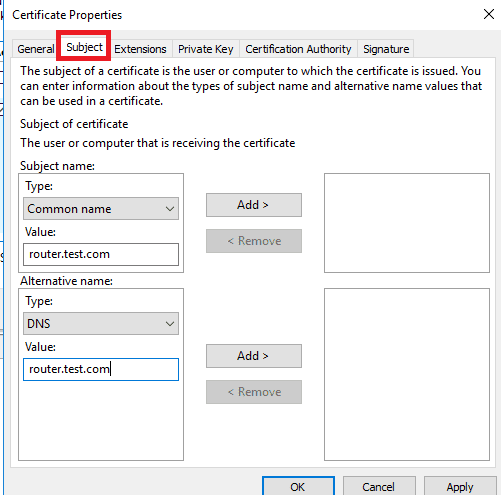
Click Subject tab > Subject Name> Common name (from drop-down menu) choose FQDN for VPN Server > Click Add
In the Alternative Name, choose DNS, set FQDN for VPN Server, Click Add
New certificate should be created as shown in image below.
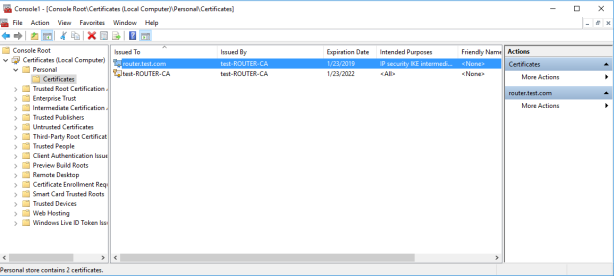
This certificate should be exported and then imported to client machine.
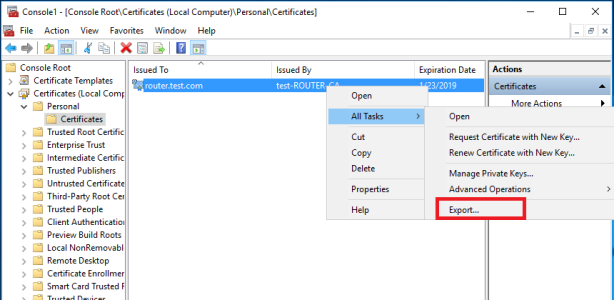
To export certificate, Right-click certificate> All tasks> Export
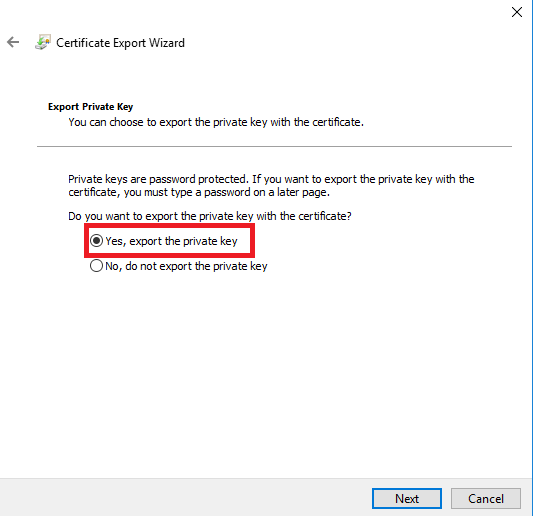
Export private key, Set password and specify file in which certificate should be saved. Copy file to client computer
To import file on client machine, certificate should be imported into Trusted Root Certification Authority on client.
Open up Run, type mmc> Add > Certificate snap-in-local computer
Right-click Trusted Root Certification Authorities> All task> import
Browse to copied file and enter password to import it.

Installing Roles
You need to add Network Policy Server and Remote Access roles on your VPN Server. Open up Server Manager > Add Roles and Features and select the following to install.
Open up Routing and Remote Access console, right-click on Server > Configure and Enable Routing and Remote Access
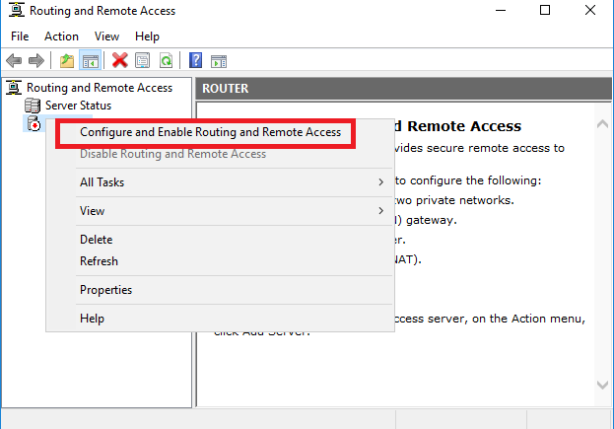
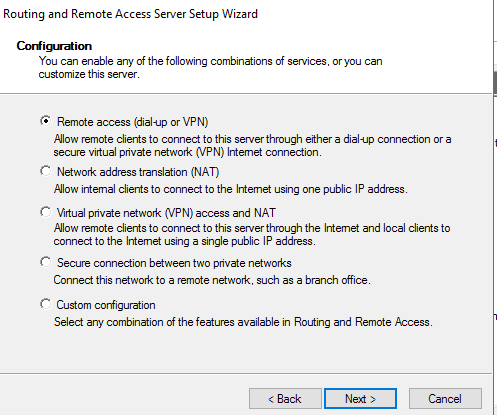
Select Remote access (dial-up or VPN)
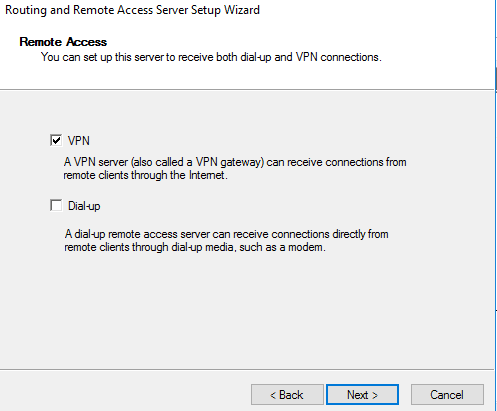
Check VPN
Select internet facing interface accordingly

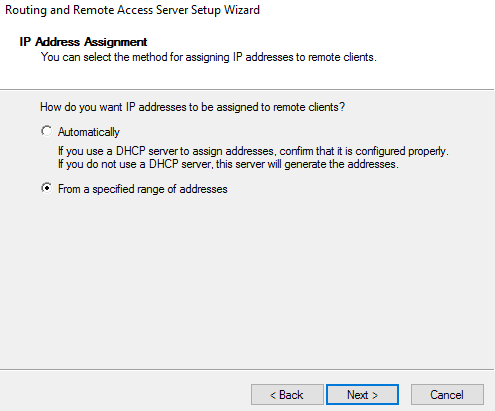
Define VPN address pool according to your environment

We’ll use NPS instead of RADIUS
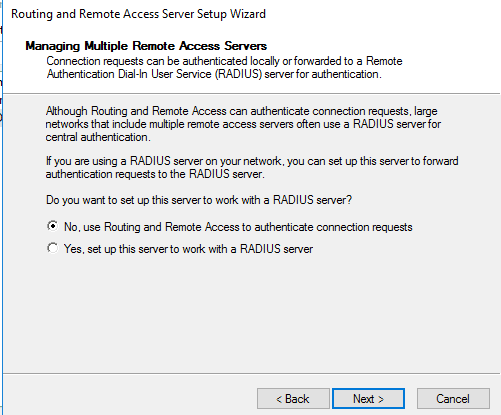
Right click Remote Access Logging> Launch NPS

Click Network Access Policies

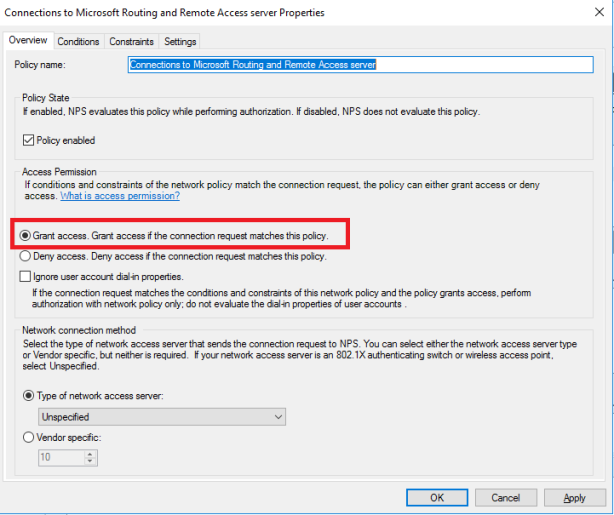
Right click Connections to Microsoft Routing and Remote Access Server > Properties

Check Grant access
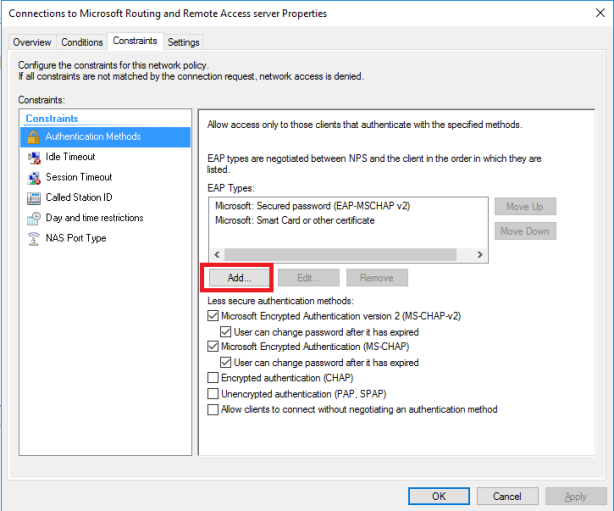
Click Constraints > Select Microsoft:Secured password (EAP-MSCHAP v2)
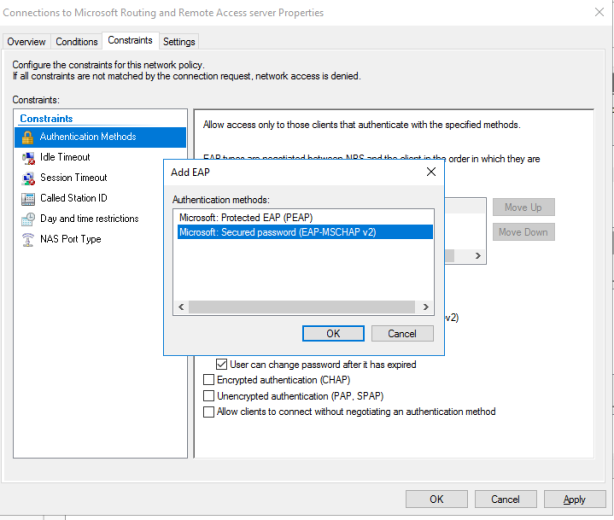
If it’s not selected Add it
Enable user VPN access
In ADUS right click Dial-in> Allow access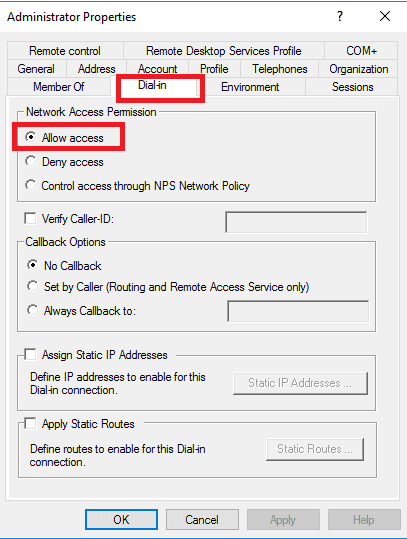
Client Setting
Open in notepad Windows/System32/Drivers/etc/hosts file and add entry for VPN server (name must be equal to one specified in SSL certificate)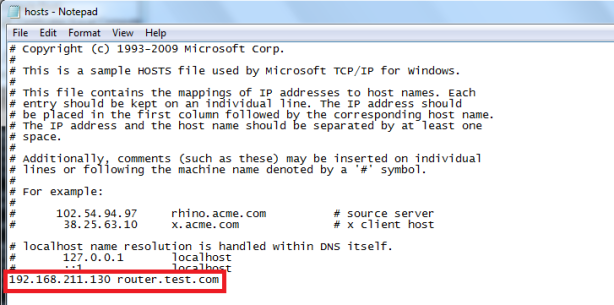
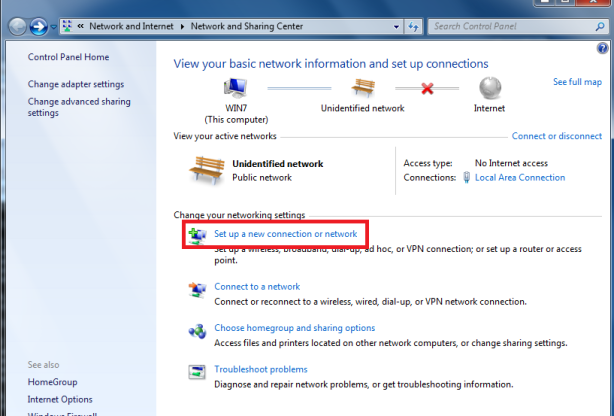
Creating VPN client connection
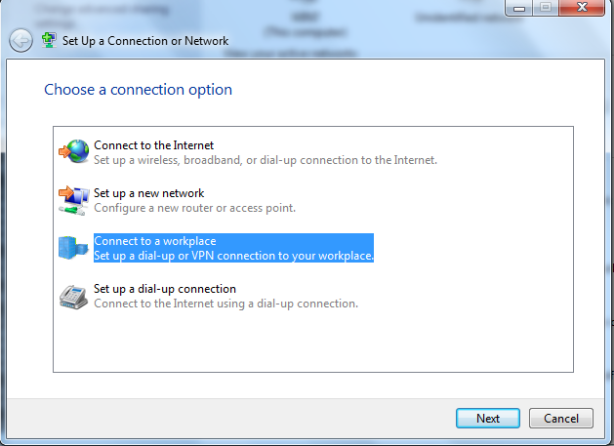
Use my internet connection (VPN)
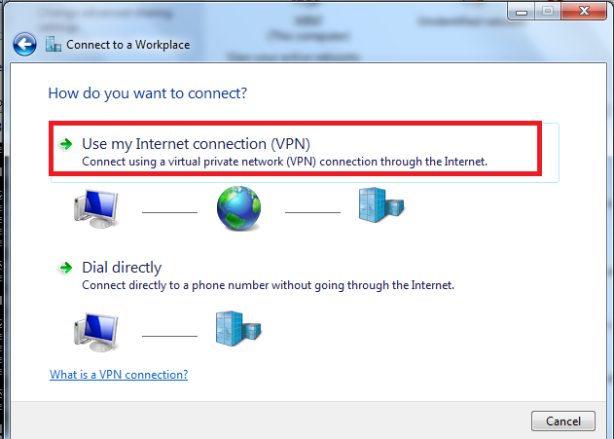
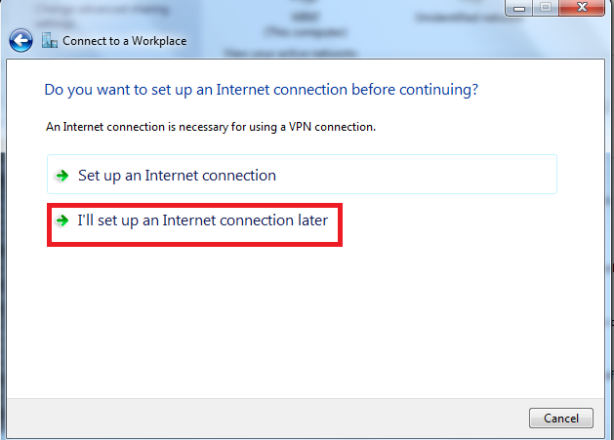
I’ll set up an internet connection later
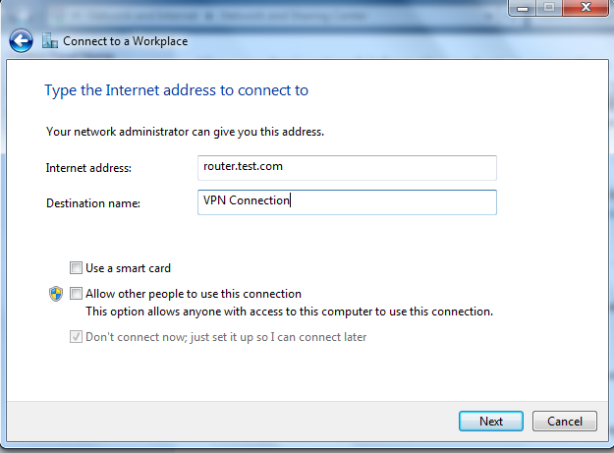
In Internet address type your VPN Server name
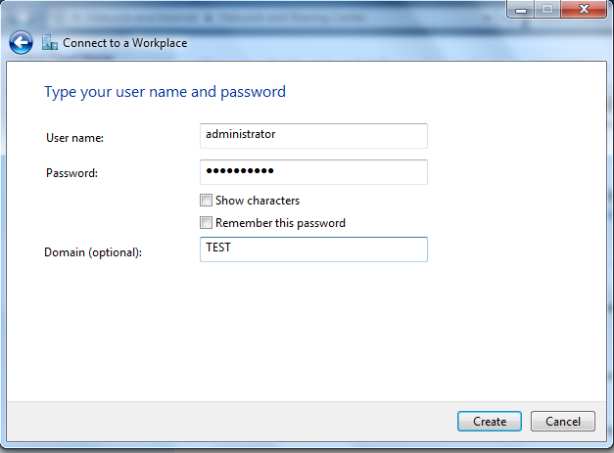
Specify username/password
In Security tab,for Type of VPN select IKEv2 > Dataencryption> Require encryption> Authentication:Microsoft:Securedpassword(EAP-MSCHAP v2)

We can see that IKEv2 is used,client got address from our VPN pool (10.10.10.3)
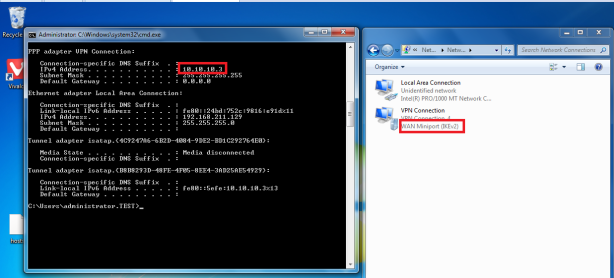
Here you can see one client is connected to VPN Server with user Administrator.
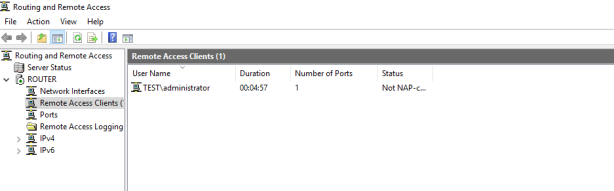
We have successfully completed VPN Server deployment on Windows Server 2016. I hope this article will be helpful to deploy VPN Server in your environment.