
Active Directory Certificate Services (AD CS) provides customizable services for issuing and managing public key infrastructure (PKI) certificates used in software security systems that employ public key technologies. The digital certificates that AD CS provides can be used to encrypt and digitally sign electronic documents and messages.
More over, these digital certificates can be used for authentication of computer, user, or device accounts on a network. Digital certificates are used to provide:
- Confidentiality - through encryption
- Integrity - through digital signatures
- Authentication - by associating certificate keys with computer, user, or device accounts on a computer network.
These certificate services were available starting in Windows 2000 and continue to be available as a server role in Windows Server 2016.
This guide walks you through the steps to deploy a single Active Directory Certificate Server on a existing domain and configuring auto enroll group policy for workstation and servers. For an enterprise environment you will need to deploy subordinate CA’s and turnoff your root CA for security.
Installing Active Directory Certificate Services Role
To begin, Open up Server Manager and click Manage > Add Roles and Features:
Click Next:
Select Role-based or feature-based installation then click Next:
Select the server you want to install this role then click Next
Select Active Directory Certificate Services then click Next:
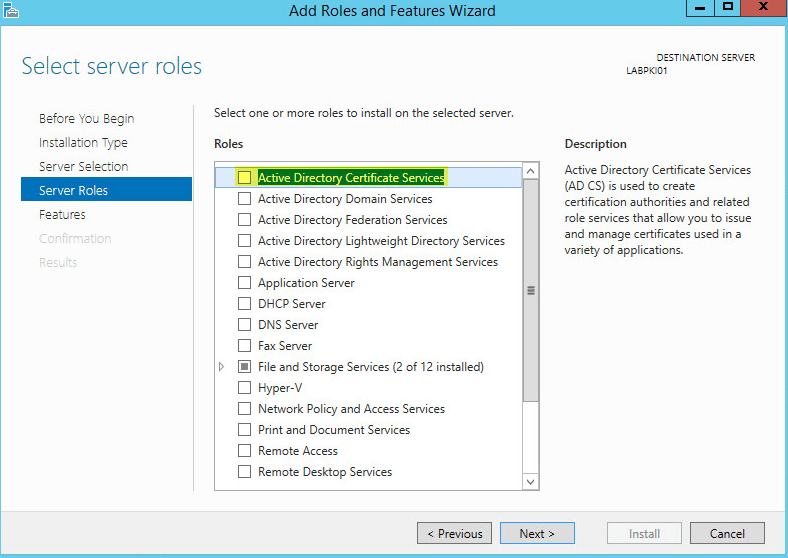
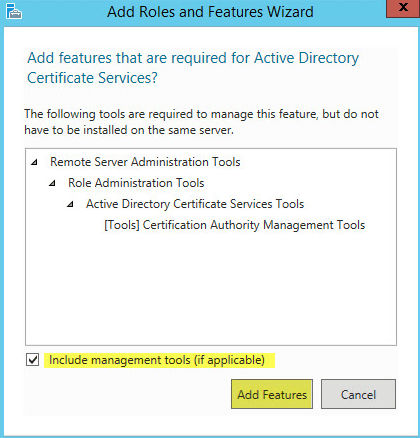
On the pop up window click the box Include management tools then Add Features:
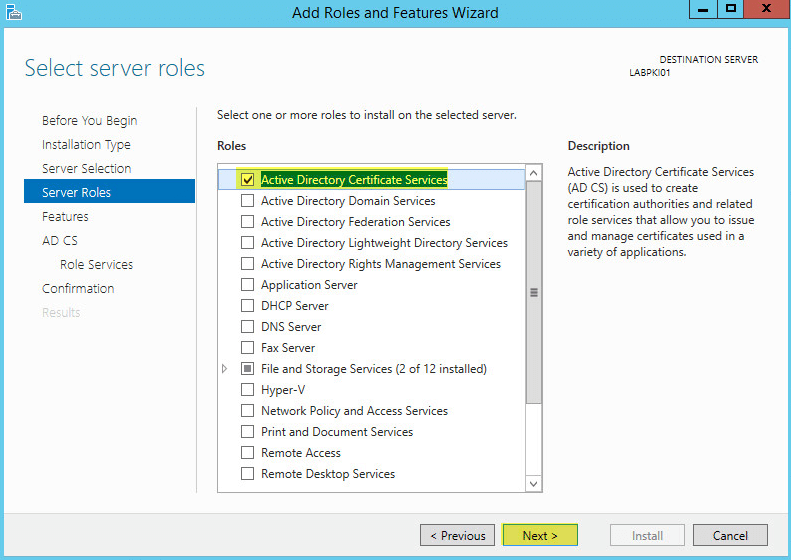
Click Next:
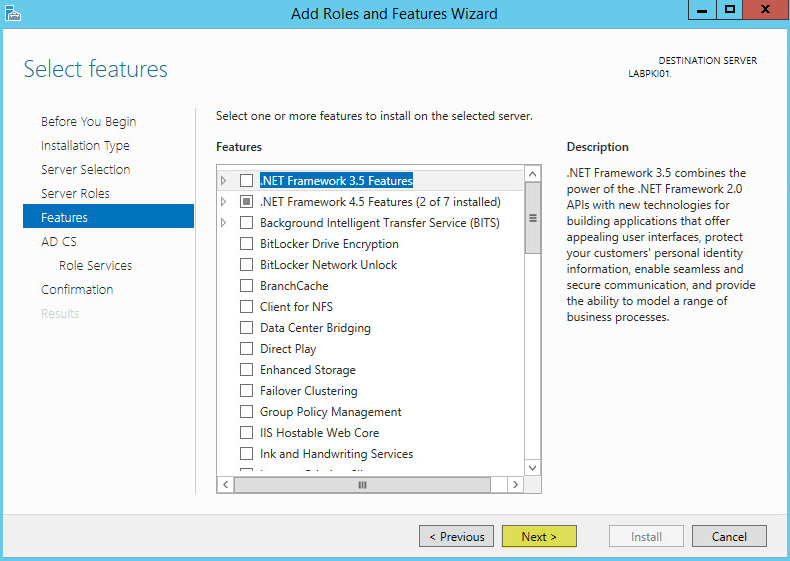
No additional Features are needed. Click Next:
Click Next:
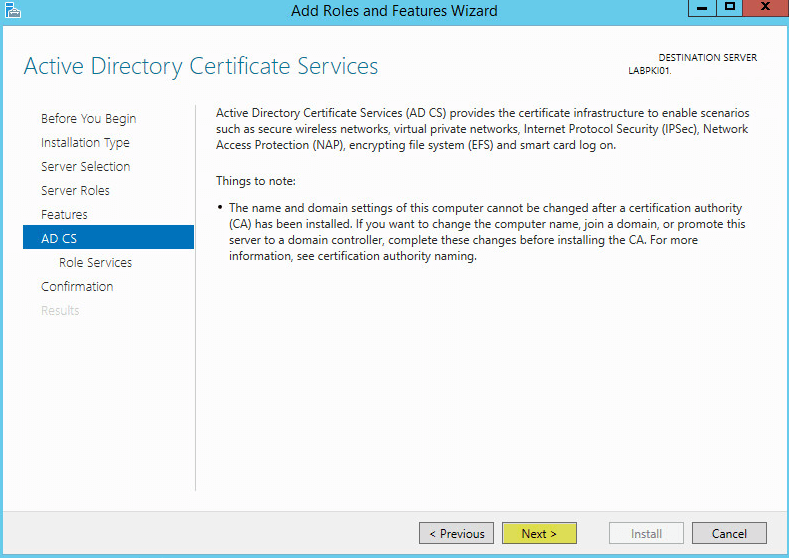
Select the services you want to enable. At a minimum enable Certificate Authority. Click Next:
A reboot was not required. Click Install:
Once the installation is complete click Close:
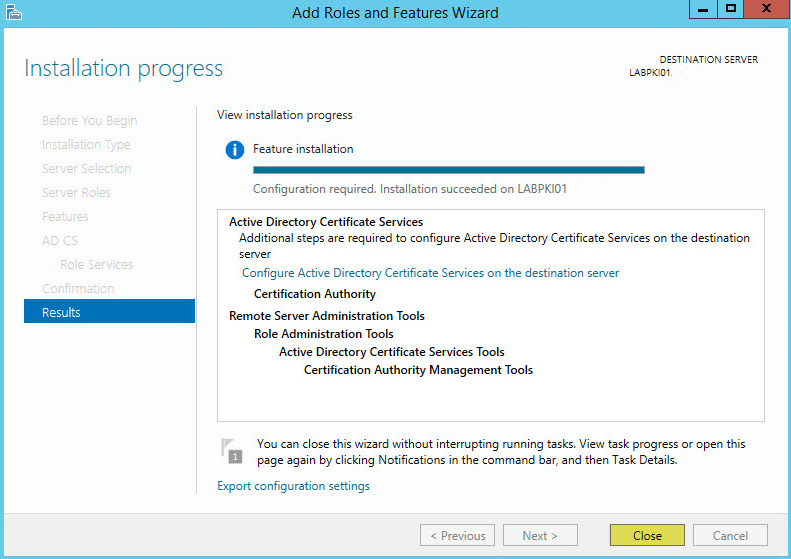
Back on Server Manager under Notifications click the message Configure the Active Directory Certificate Services on this server:
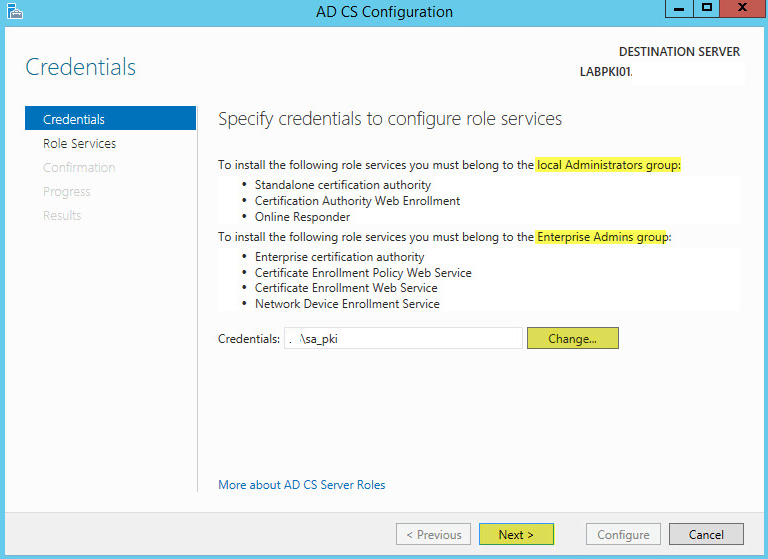
Select a user account that has the permissions depending on the role services you selected above. Click Next:
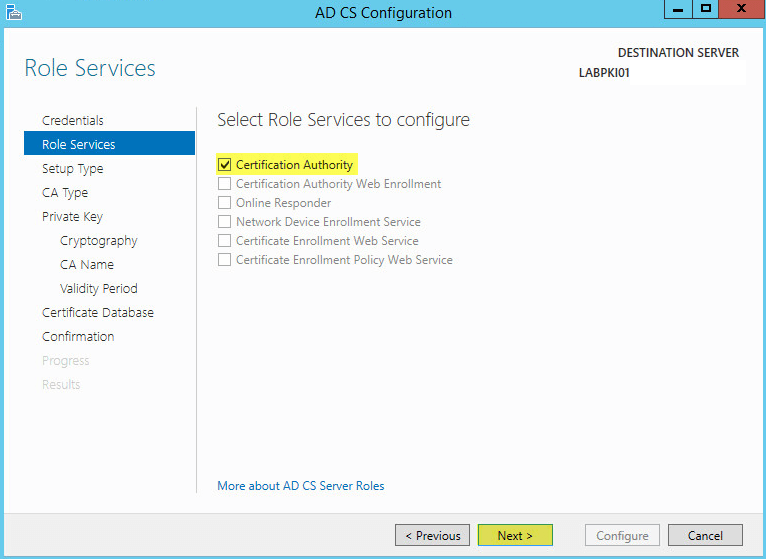
In my example I will be configuring the Certification Authority. Click Next:
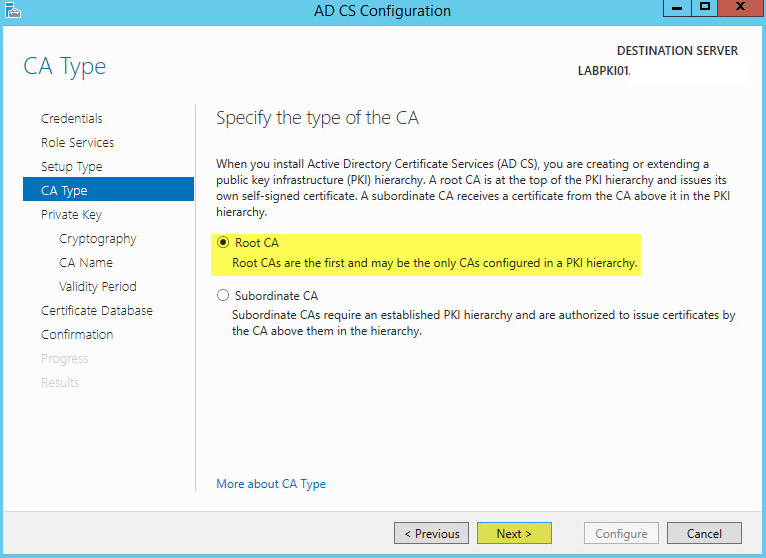
Since I am using a domain controller for this particular role, I will select Enterprise CA. Click Next:
Note: If you are installing CS role on a standalone server then go with Standalone CA

This is our first PKI server so I will select Root CA. Click Next:
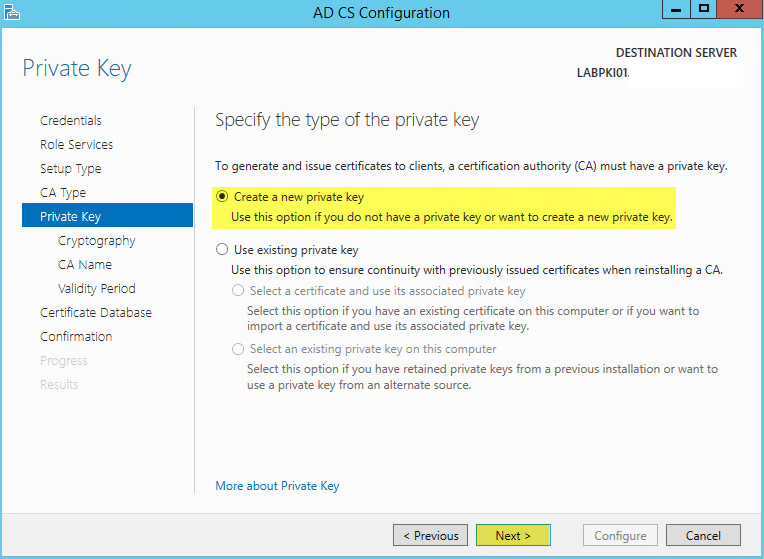
Create a new private key then click Next:
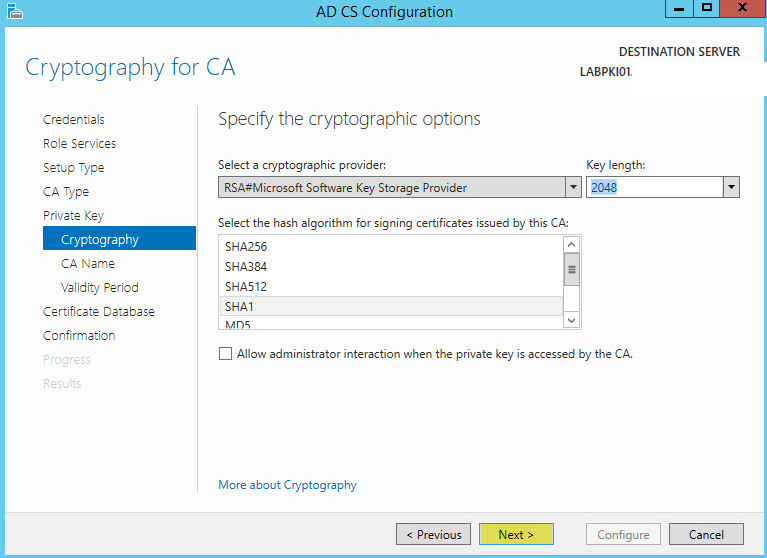
Enter your cryptographic options then click Next:
Note: Do not select SHA1 as it is being deprecated by all browsers and Microsoft Server Authentication; use SHA256 instead.
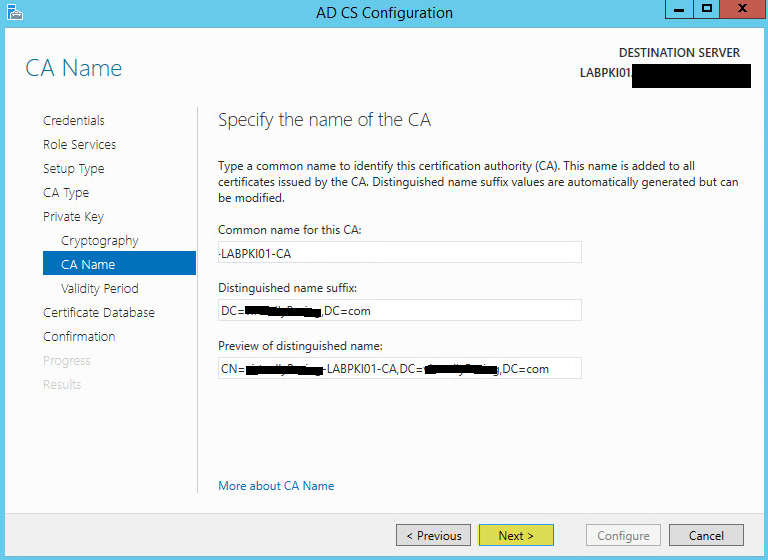
The fields should be pre-populated but you can change the Common name if you wish. Click Next:
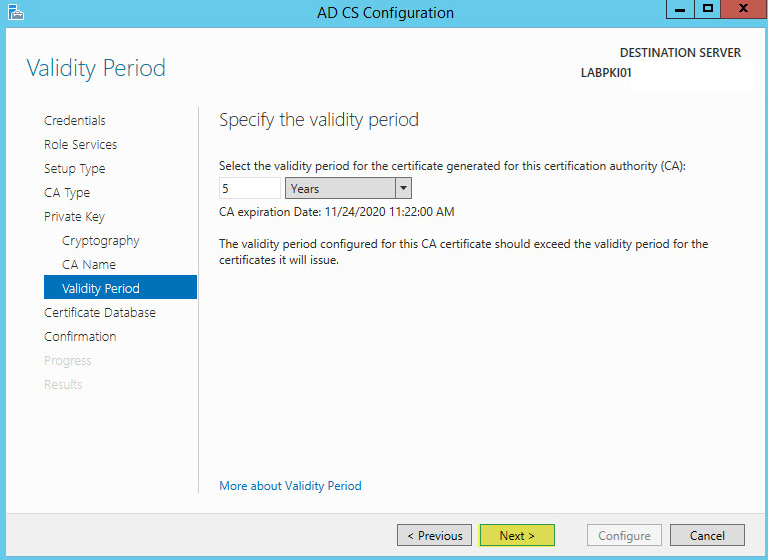
Enter a validity period. This is how often the CA certificate will expire and will need to be renew on subordinate CA (if applicable).
Take note of the message: The validity period configured for the CA certificate should exceed the validity period for certificates it will issue.
Click Next:
We recommend leaving these as defaults. Click Next:
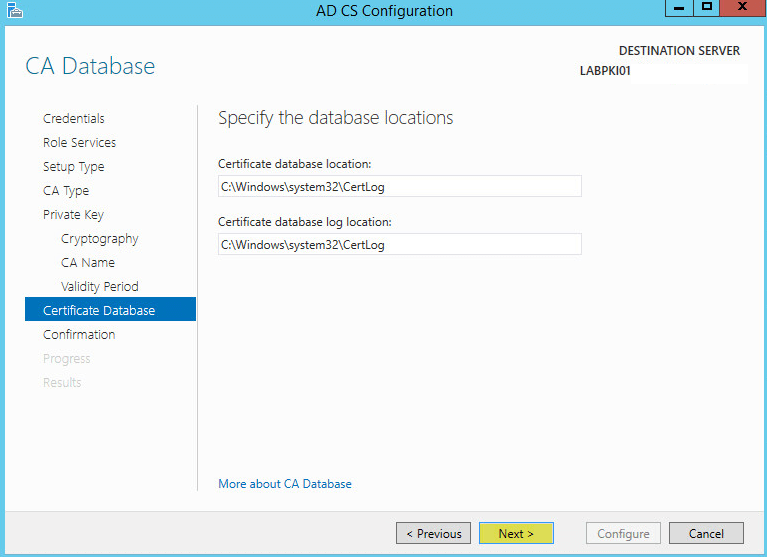
Make sure the summary is correct then click Configure:
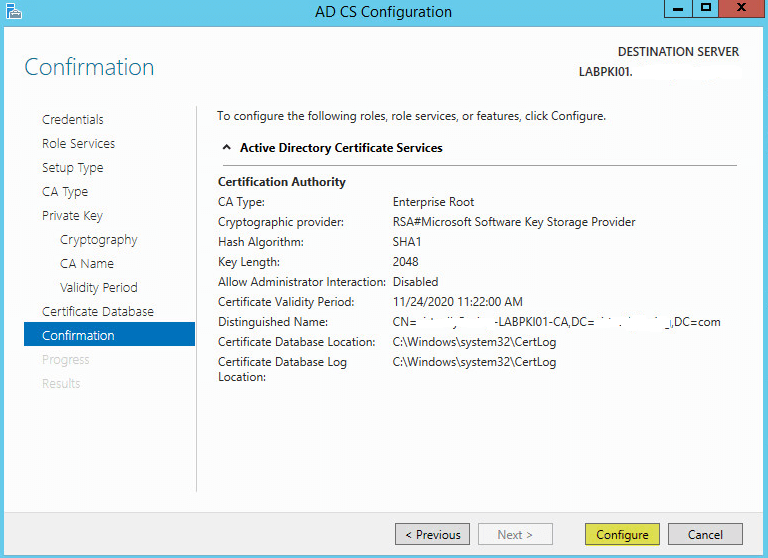
Click Close:
Creating Certificate Template for Workstation and Client Authentication
This step is to create a certificate template that will enable your domain computers to request certificates from your PKI server.
Open up Control Panel then go to Administrative Tools > Certification Authority:
Right click Certificate Templates then Manage:
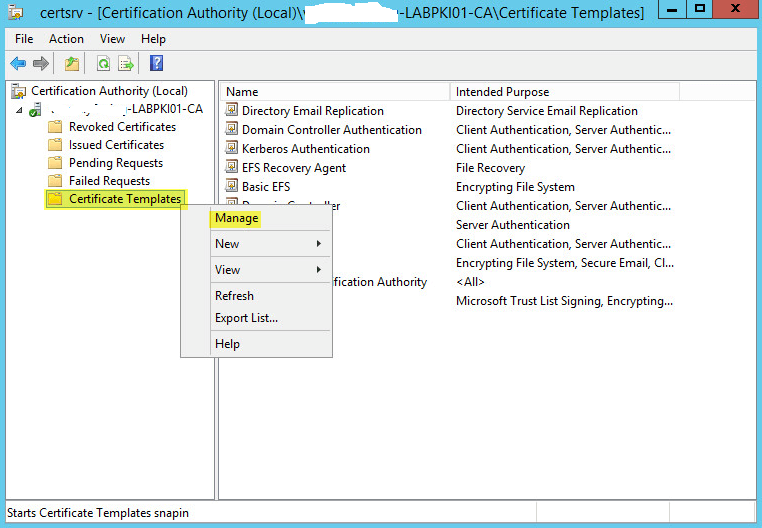
Scroll down to Workstation Authentication, right click then select Duplicate Template:
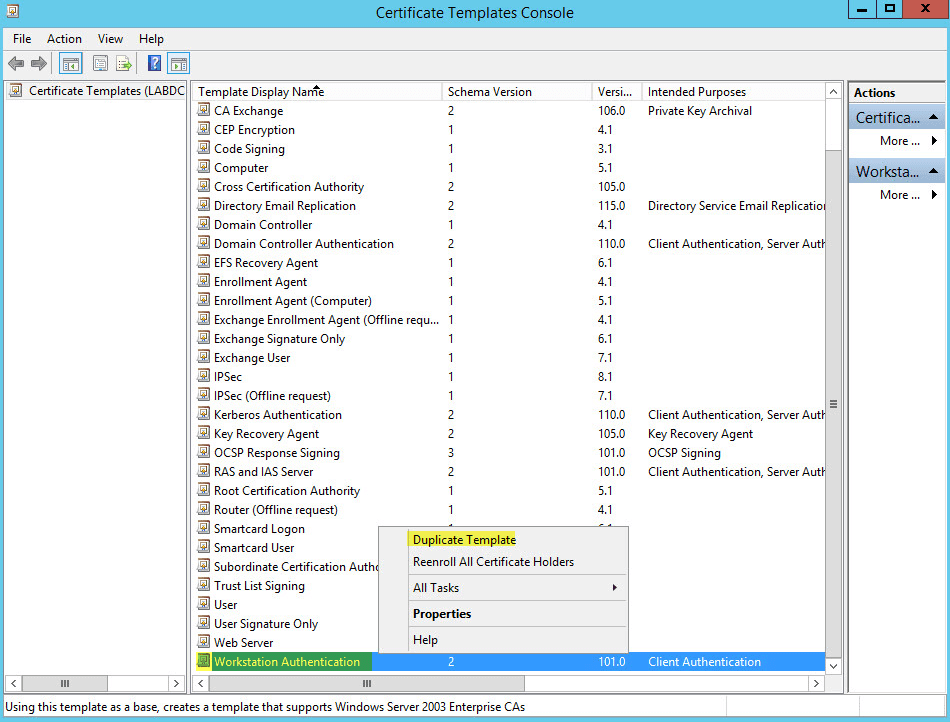
On the General Tab enter a template display name then select a validity period. Click the two boxed options:
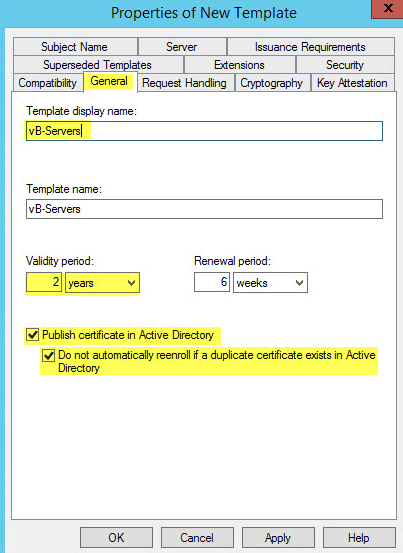
On the Security tab add Domain Computers as this will give permission to your Domain Computers. Check the boxes for Read and Autoenroll:
On the Extensions tab click Application Policies then Edit:
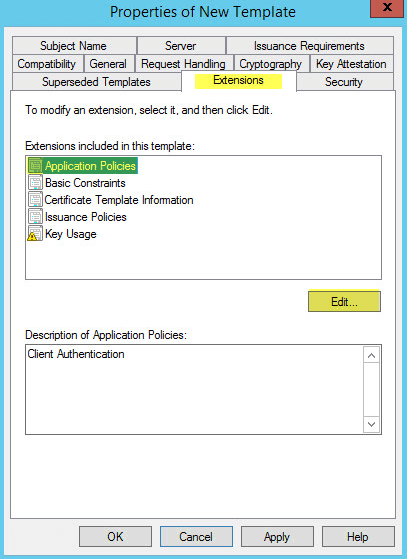
Click Add > Server Authentication then Ok
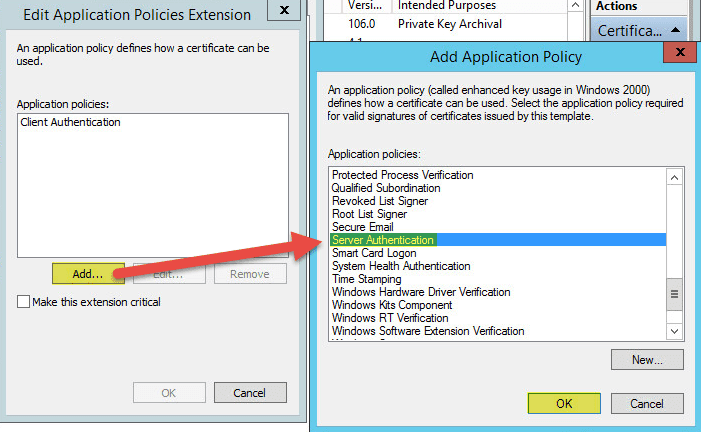
Make sure Server Authentication is selected then click OK
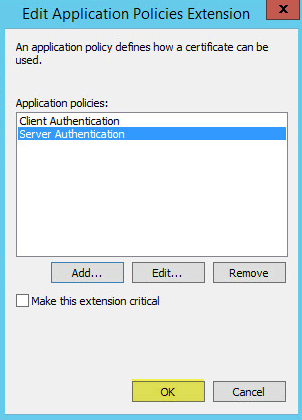
On the Subject Name tab click the DNS name box to add the DNS name to the SAN of the certificate. Click Apply and OK
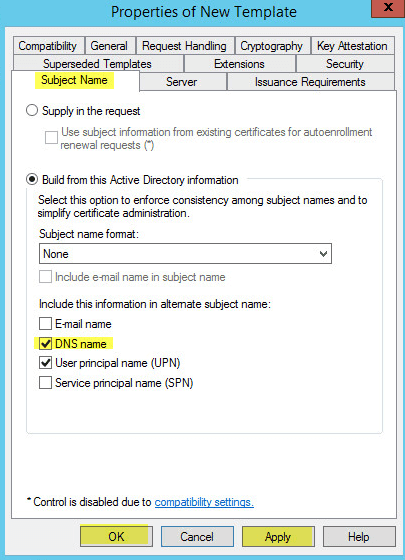
You will now have a new template with the intended purposes of Client Authentication, Server Authentication. You can now close the Certificate Templates Console window.
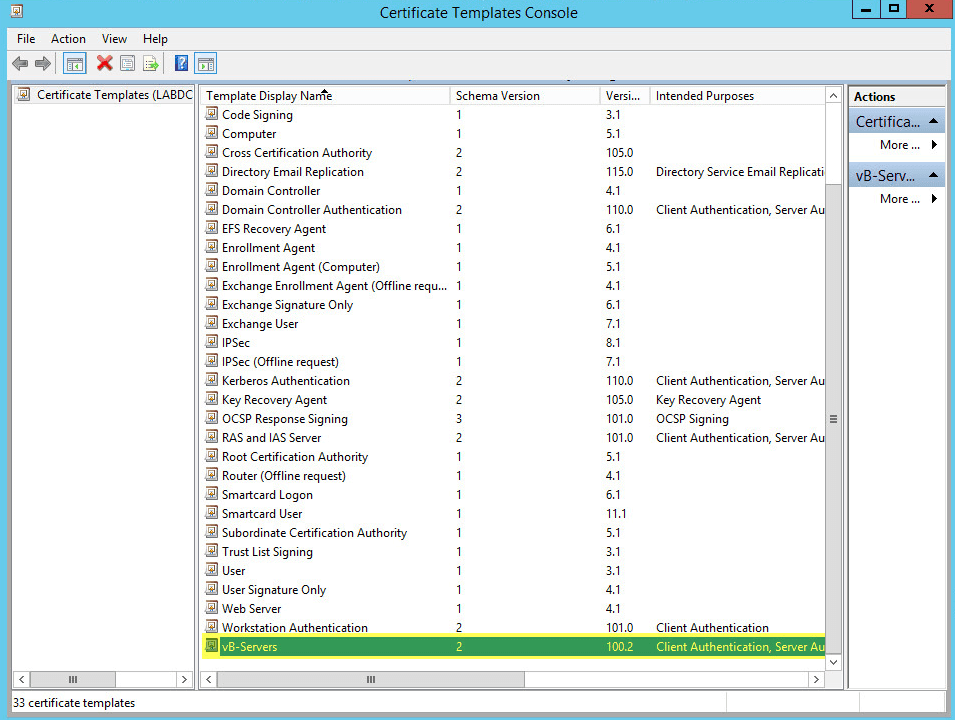
Back on the Certification Authority window, right click Certification Template > New > Certificate Template to Issue
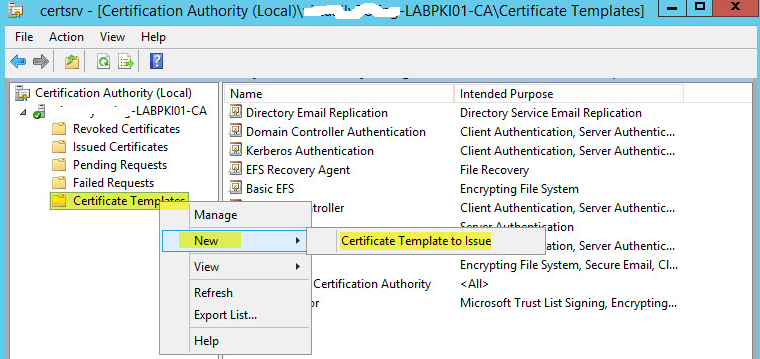
Select the Certificate Template we created then click OK. The custom template should now show under Certificate Templates.
Configuring Group Policy for Automatic Certificate Enrollment:
This step is to create the group policy to automate certificate enrollment on computers through your PKI server.
On your Domain Controller open Control Panel then Administrative Tools > Group Policy Management:
You can edit the Default Domain Policy so all computers are configured to request a certificate from your PKI or you can create a policy in a specific OU. I chose to create a new policy for my Windows Servers OU.
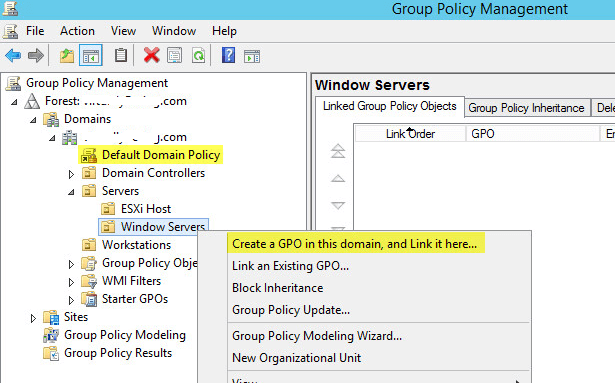
Enter a name and click OK
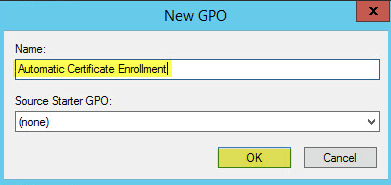
Now right click the new policy then click Edit:
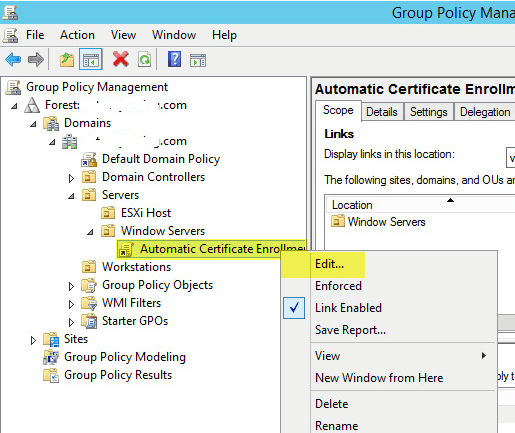
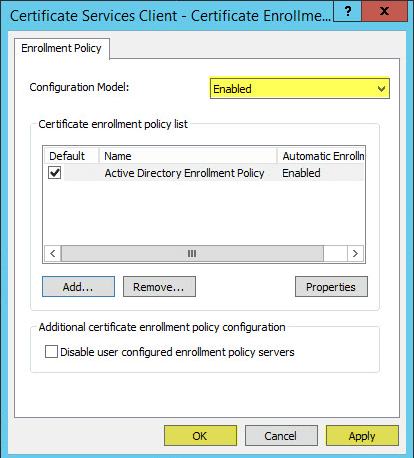
Scroll down to Public Key Policies. In the right pane right click Certificate Services Client > Certificate Enrollment Policy then Properties:
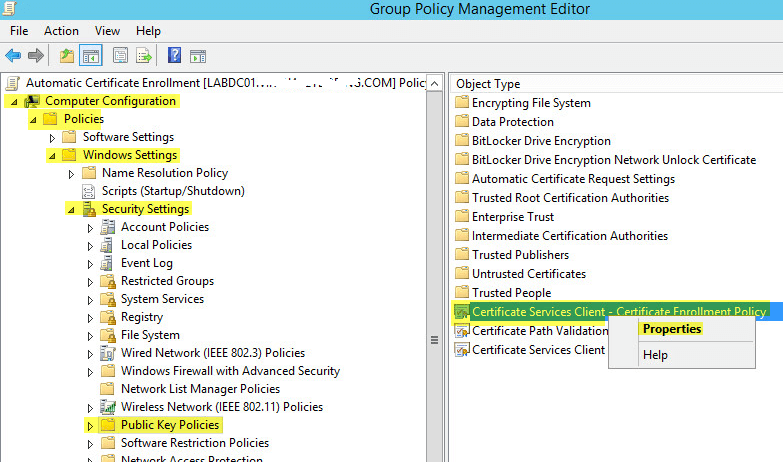
Change the drop down menu to Enabled then click Apply > OK
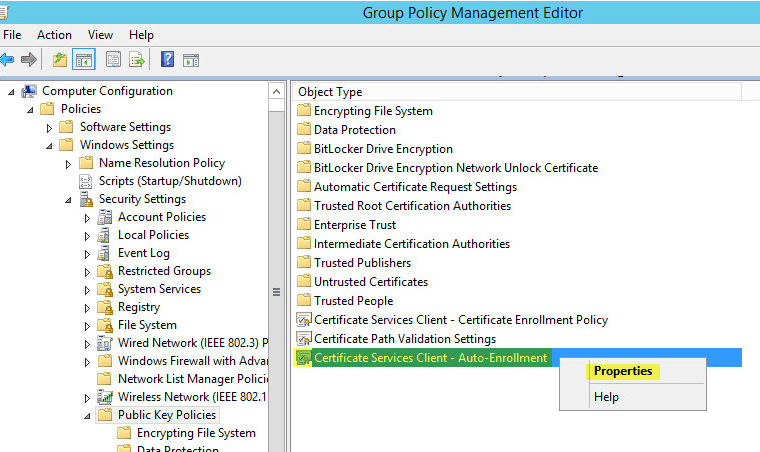
Now right click Certificate Services Client > Auto-Enrollment then Properties:
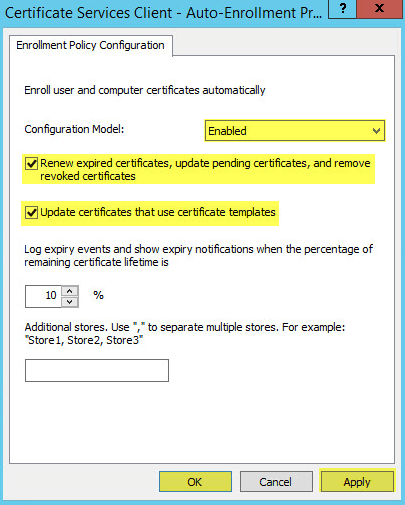
Change the drop down menu to Enabled and check the two boxes. Click Apply then Ok. You can now exit the Group Policy Management Editor:
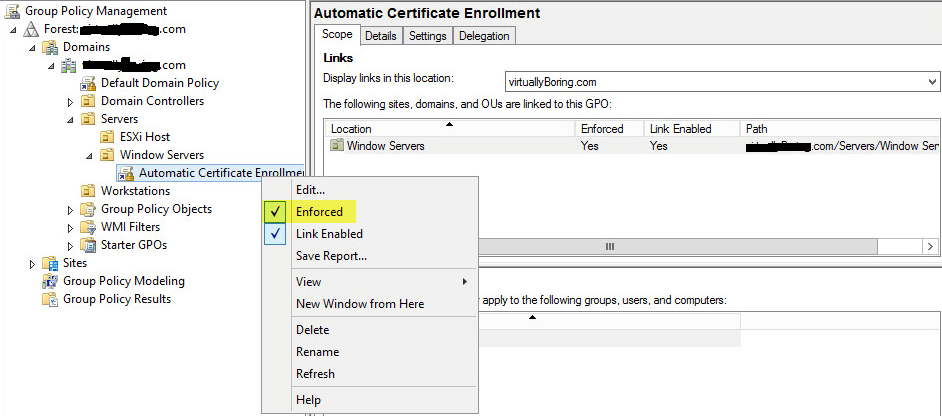
Right click your Policy then click Enforced to enable the policy:
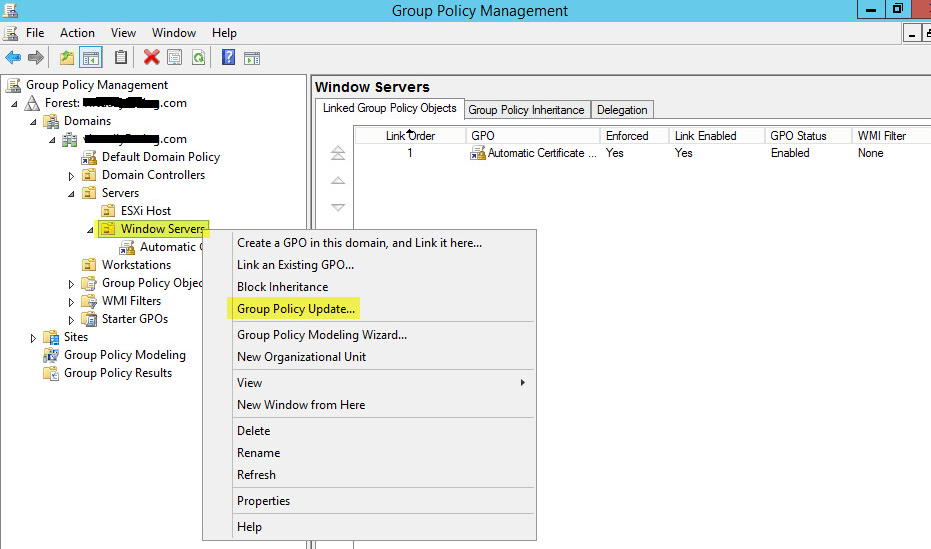
Again right click the OU and click Group Policy Update to accelerate getting the policy pushed out.
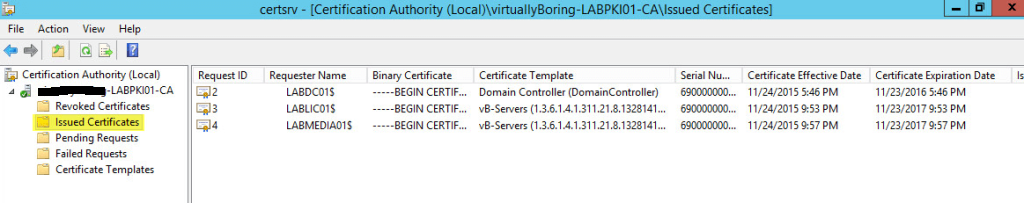
Go back on your PKI server if you open Certification Authority and go to Issued Certificates you will start seeing your computers have requested and obtained a certificate. If you don’t see anything yet, give it some time and refresh later.
You have successfully set up Certificate Server in your environment.