
Active Directory Federation Services provides access control and single sign on across a wide variety of applications including Office 365, cloud based SaaS applications, and applications on the corporate network.
- For the IT organization, it enables you to provide sign on and access control to both modern and legacy applications, on premises and in the cloud, based on the same set of credentials and policies.
- For the user, it provides seamless sign on using the same, familiar account credentials.
- For the developer, it provides an easy way to authenticate users whose identities live in the organizational directory so that you can focus your efforts on your application, not authentication or identity.
AD FS 2016 enables three new options for sign on without passwords, enabling organizations to avoid risk of network compromise from phished, leaked or stolen passwords.
Sign in with Azure Multi-factor Authentication
AD FS 2016 builds upon the multi-factor authentication (MFA) capabilities of AD FS in Windows Server 2012 R2 by allowing sign on using only an Azure MFA code, without first entering a username and password.
- With Azure MFA as the primary authentication method, the user is prompted for their username and the OTP code from the Azure Authenticator app.
- With Azure MFA as the secondary or additional authentication method, the user provides primary authentication credentials (using Windows Integrated Authentication, username and password, smart card, or user or device certificate), then sees a prompt for text, voice, or OTP based Azure MFA login.
- With the new built-in Azure MFA adapter, setup and configuration for Azure MFA with AD FS has never been simpler.
- Organizations can take advantage of Azure MFA without the need for an on premises Azure MFA server.
- Azure MFA can be configured for intranet or extranet, or as part of any access control policy.
Password-less Access from Compliant Devices
AD FS 2016 builds on previous device registration capabilities to enable sign on and access control based the device compliance status. Users can sign on using the device credential, and compliance is re-evaluated when device attributes change, so that you can always ensure policies are being enforced. This enables policies such as
- Enable Access only from devices that are managed and/or compliant
- Enable Extranet Access only from devices that are managed and/or compliant
- Require multi-factor authentication for computers that are not managed or not compliant
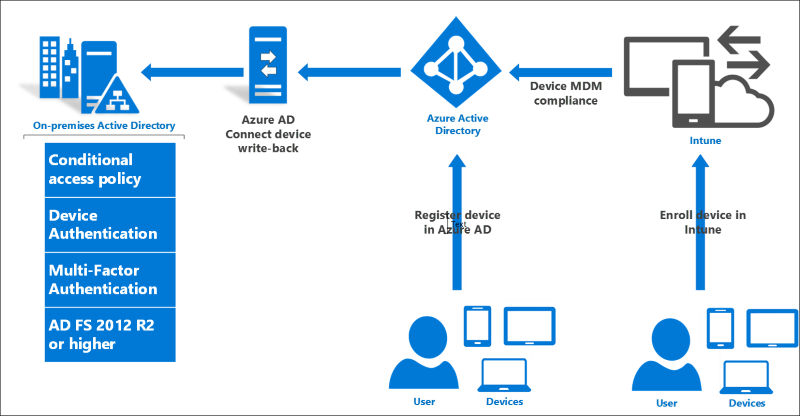
- AD FS provides the on premises component of conditional access policies in a hybrid scenario. When you register devices with Azure AD for conditional access to cloud resources, the device identity can be used for AD FS policies as well.
Sign in with Microsoft Passport
Windows 10 devices introduce Windows Hello and Microsoft Passport for Work, replacing user passwords with strong device-bound user credentials protected by a user's gesture (a PIN, a biometric gesture like fingerprint, or facial recognition). AD FS 2016 supports these new these new Windows 10 capabilities so that users can sign in to AD FS applications from the intranet or the extranet without the need to provide a password.
This guide walks you through the the steps to installing and configuring the Active Directory Federation Services (AD FS) server role on Windows Server 2016.
Installing Active Directory Federation Services Role
To begin, Open up Server Manager and click Manage click Add Roles and Features:
Click Next:
Role-based or feature-based installation should be selected then click Next:
Select the server you want to install this role then click Next:
Note: Web Application Proxy role and AD FS cannot be installed on the same computer.
Select Active Directory Federation Services then click Next:
No additional Features are needed. Click Next:

Click Next:
The AD FS role does not required a reboot. Click Install:
Once complete click Close:
Post-deployment Configuration
Back on Server Manager under Notifications click the message Configure the federation service on this server:
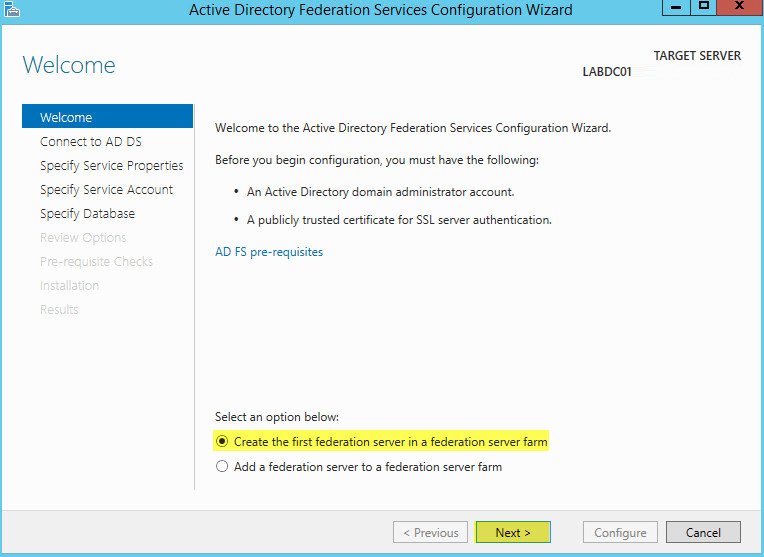
Since this is our first AD FS server select the first option then click Next:
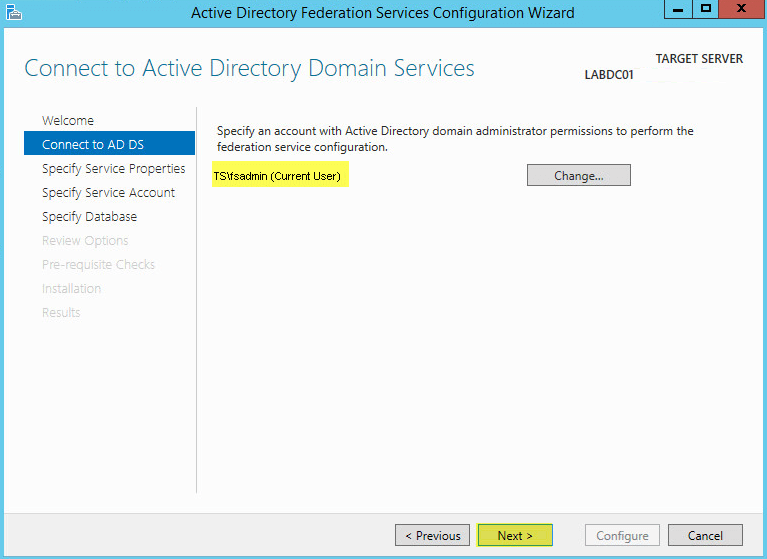
Ensure the account you are logged into has Active Directory Domain Admin permissions. If not then click Change. Click Next to continue:
SSL Certificate: On the drop down menu you will see the certificates installed on the server. You can use the default self signed or use one you create. Make sure you have it in .pfx format.
Federation Service Name: Give your AD FS a FQDN name.
Federation Service Display Name: Enter a display name
Click Next to proceed:
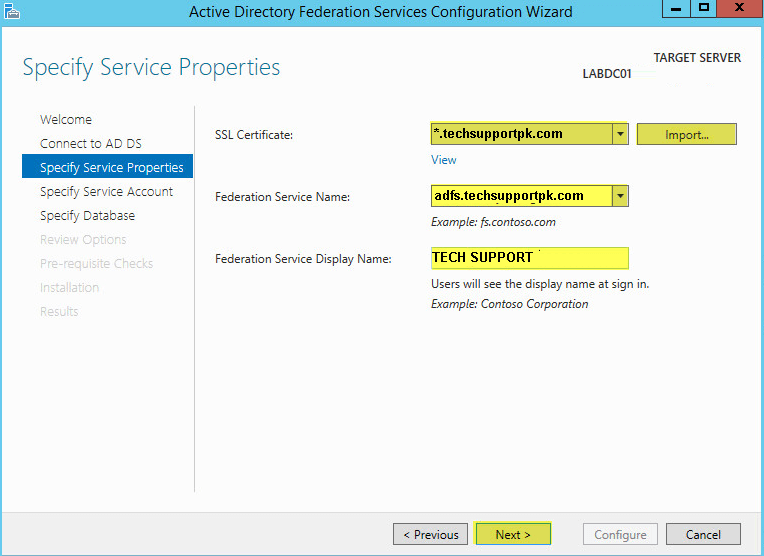
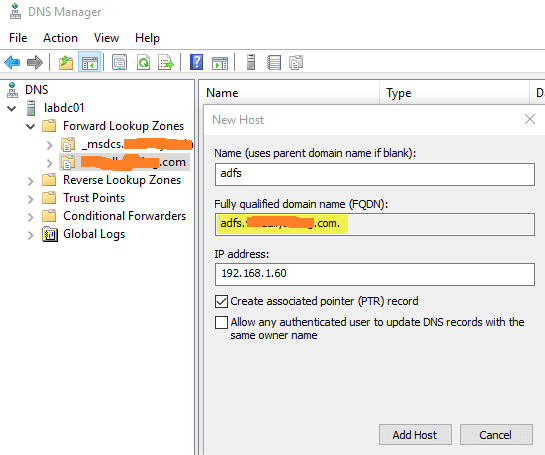
Note about Federation Service Name: If you are installing AD FS on a Domain Controller or want to use a different FQDN for AD FS than the server you will need to ensure the name you enter has a DNS Record created.
Since this is my test lab I am adding AD FS on my Domain Controller and needed to create a DNS entry
Note about SSL Certificate: If you imported a certificate you will see it added to your Personal Certificates.

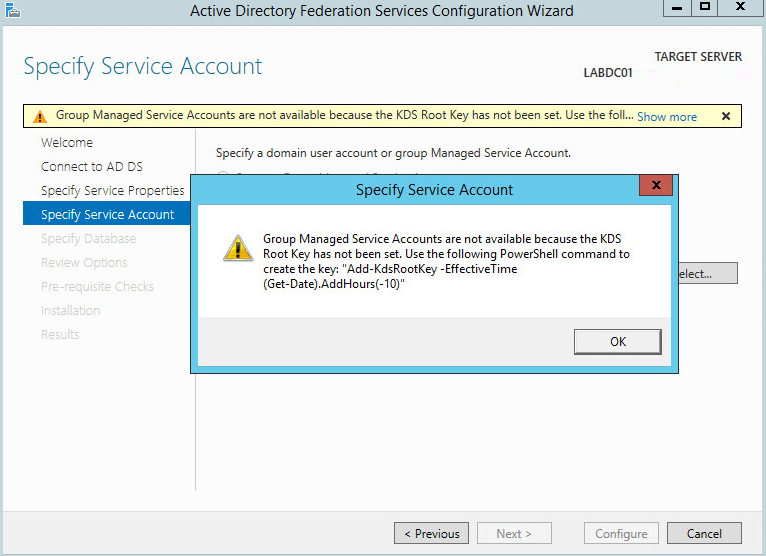
On the Specify Service Account tab you may get the following message:
If you want the Wizard to create a Service Account for you then proceed to the PowerShell window below. If you want to create a Service Account manually you can add it by selecting the second option.
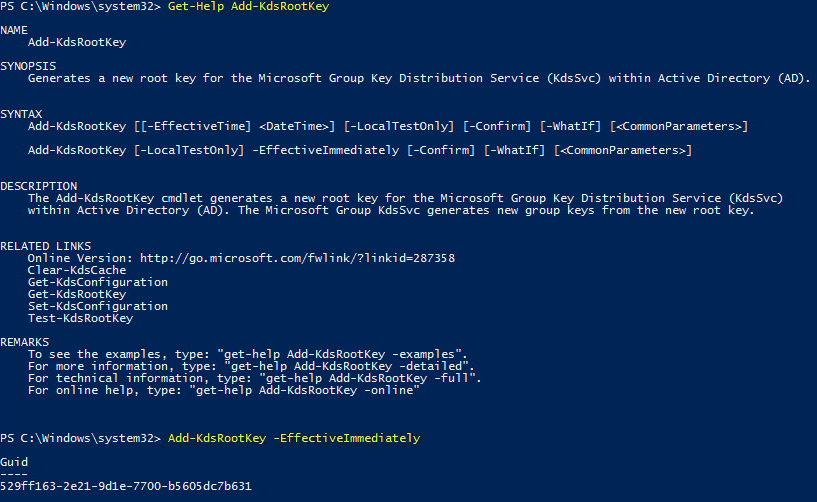
To get more info about the command
To generate root key
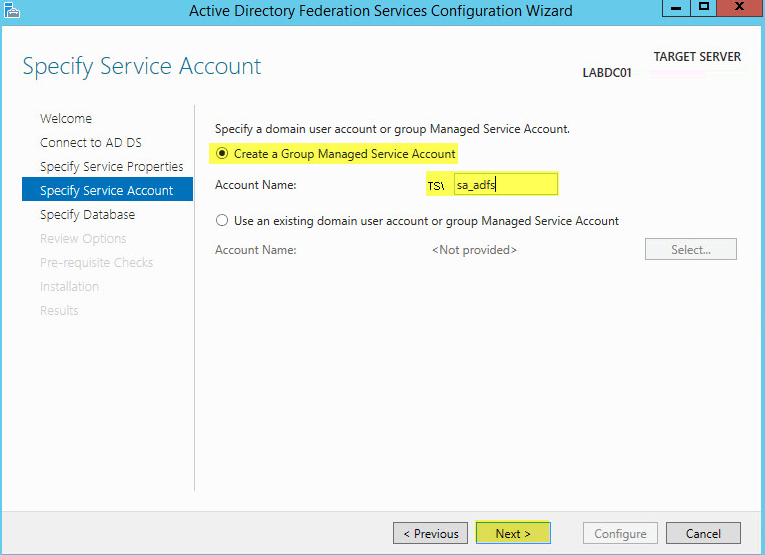
Enter the Service Account you want to use and click Next:
Note: Ensure this user account is added to the local administrators group of your AD FS server. It is required to setup Microsoft Web Application Proxy.
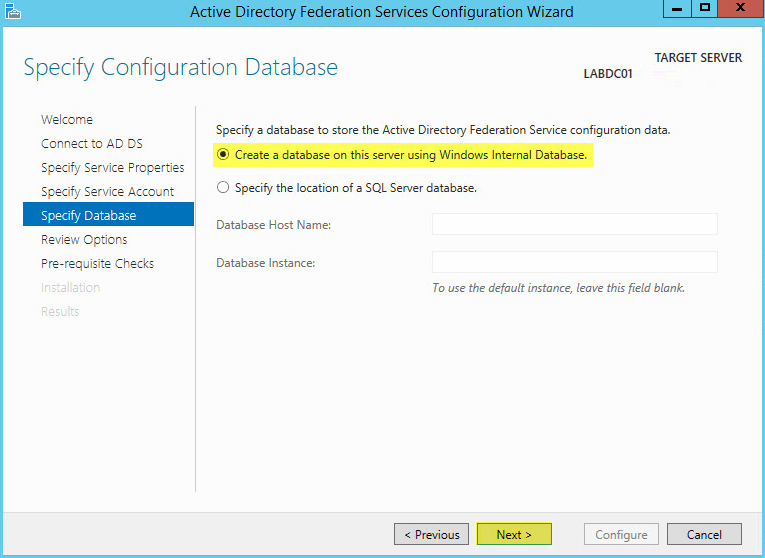
You have the option of using a Windows Internal Database (WID) or SQL Server. If you have a small environment/lab then use WID. If you have a large environment use a SQL database. Click Next:
Note: WID is a limited version of SQL Express that doesn’t have a GUI or management interface. The WID database is a file (SUSDB.dbf) stored in C:\Windows\wid\data\
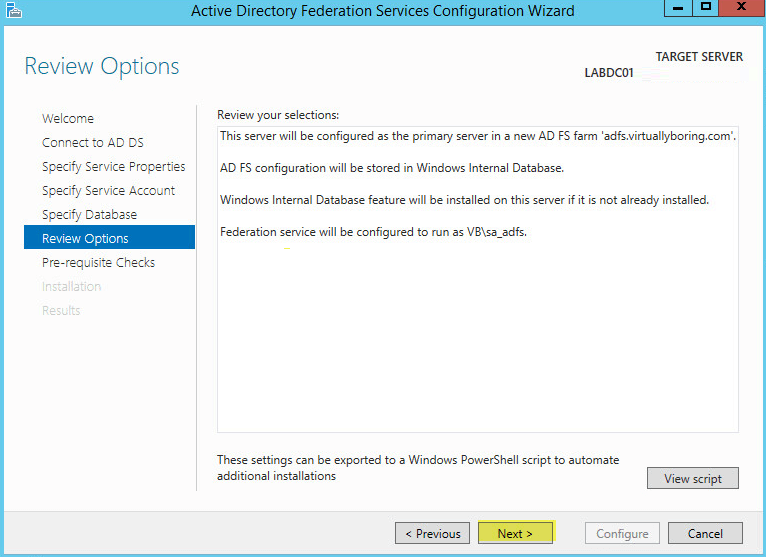
Click Next:
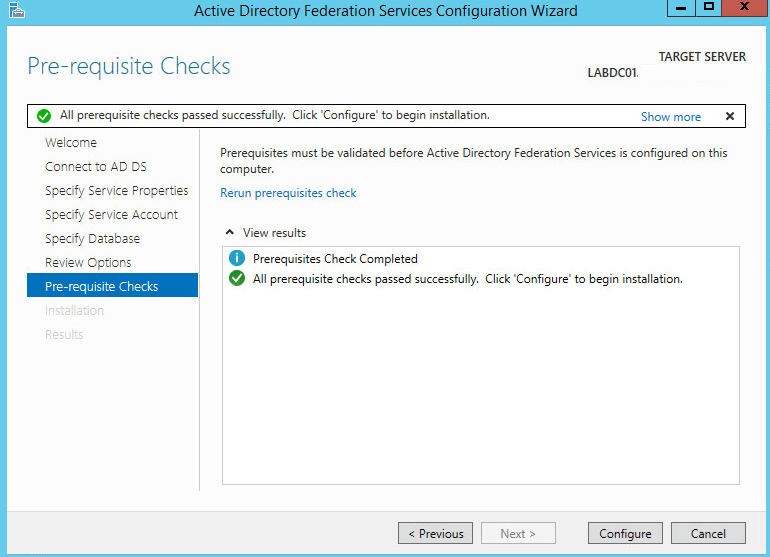
If everything fine click Configure:
Once complete click Close
Active Directory Federation Services is now installed and is ready for testing.
Open up a web browser and navigate to the URL https://ADFS-FQDN/adfs/ls/ldpintiatedSignOn and click Sign In:
Enter your domain credentials, once logged in, the following page will show up![]()

That's it.